I will be installing an enterprise pool that consists of two Front-End Servers.
Servers :
DC-01.chahla.local (Domain Controller, Certificate Authority)
Lync-fe01.chahla.local (Lync Front End Server 01)
Lync-fe02.chahla.local (Lync Front End Server 02)
SQL-01.chahla.local (SQL Back End Server 01 for RTC Instance)
SQL-02.chahla.local (SQL Back End Server 02 for LyncMonitoring, LyncArchiving and Persistent Chat Instances) (not used in this article – i will be using it for other articles)
Pre-requisites:
-Active Directory, DNS, Active Directory Certificate Services (Certificate Authority)
(From Dashboard – > Add Roles And Features)
http://technet.microsoft.com/en-us/library/gg398686.aspx
Features
.NET Framework 3.5 Features (All)
.NET Framework 4.5 (ALL)
Message Queuing
Message Queuing Services
Remote Server Administration Tools
Role Administration Tools
AD DS and AD LDS Tools
User Interface and Infrastructure
Desktop Experience
Windows Identity Foundation 3.5
Web Server (IIS)
Role Services
Common Http Features Installed
Default Document
HTTP Errors
Static Content
Health and Diagnostics
HTTP Logging
Logging Tools
Tracing
Performance
Static Content Compression
Dynamic Content Compression
Security
Request Filtering
Client Certificate Mapping Authentication
Windows Authentication
Application Development
.NET Extensibility 3.5
.NET Extensibility 4.5
ASP.NET 3.5
ASP.NET 4.5
ISAPI Extensions
ISAPI Filters
Management Tools
IIS Management Console
IIS Management Scripts and Tools
Restart the server after installing the prerequisites.
- Open the installation media, Microsoft Visual C++ 2012 Redistributable will be installed when you launch the installer.
- Browse to the location where you want to install and click Install.

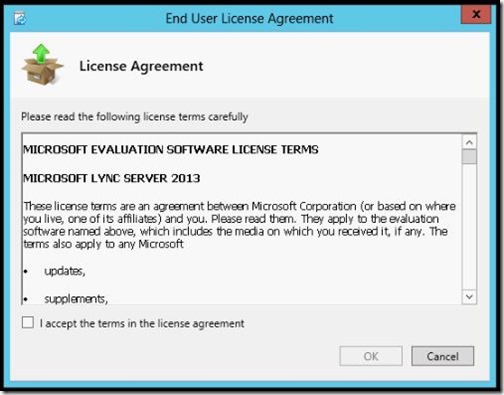
- Accept the EULA.
- Core components will install.

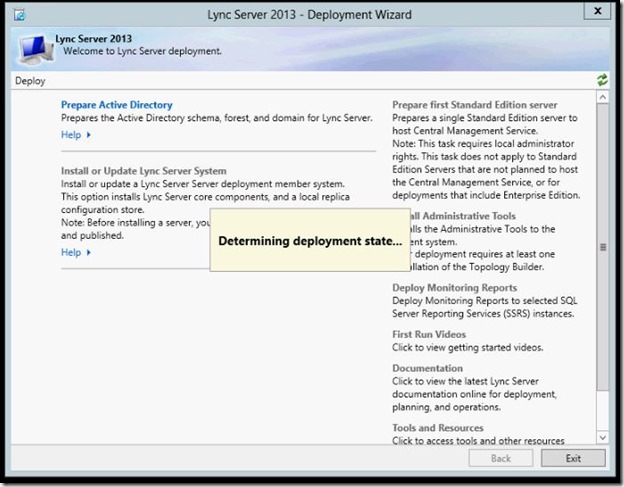
- Lync Server 2012 – Deployment Wizard will appear.
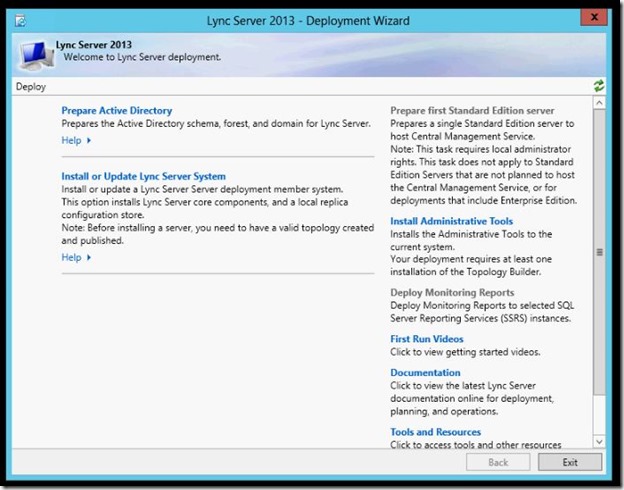
- The first thing that we will do is to Prepare Active Directory. Click Prepare Active Directory.
- On the right side of Prepare Schema, click Run.

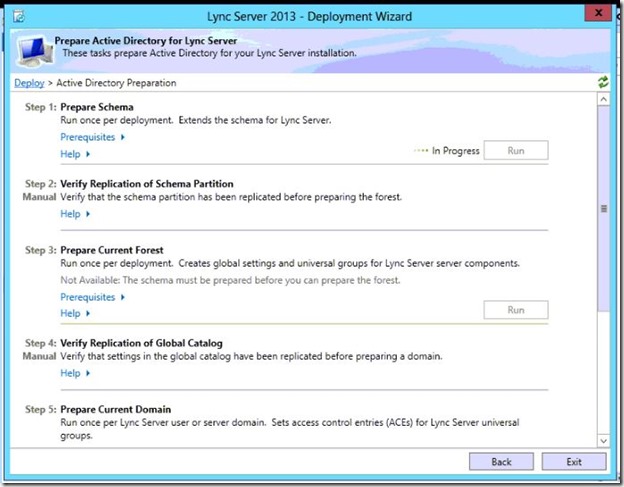
- Click Next.

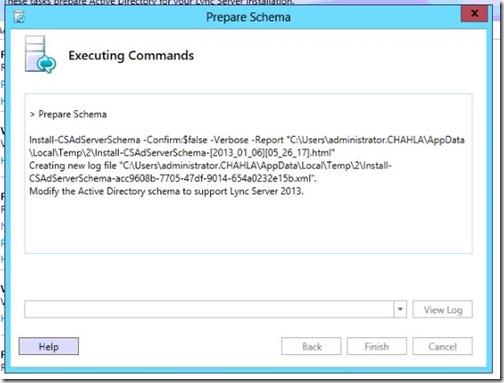
- Schema preparation finishes, click Finish.
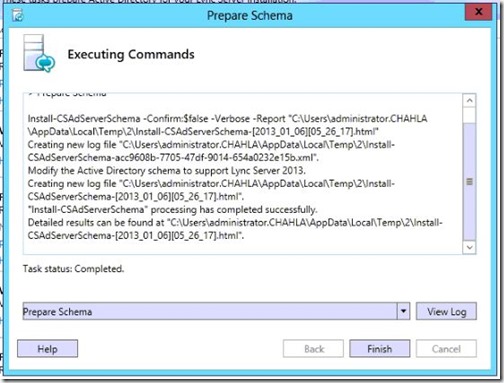
- On the right side of Prepare Current Forest, click Run.
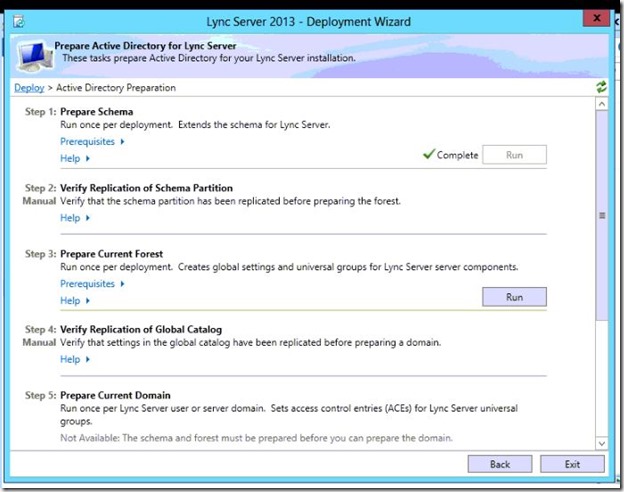
- Click Next.
- Select Local Domain, then click Next.

- Forest preparation finishes, click Finish.
- On the right side of Prepare Current Domain, click Run.

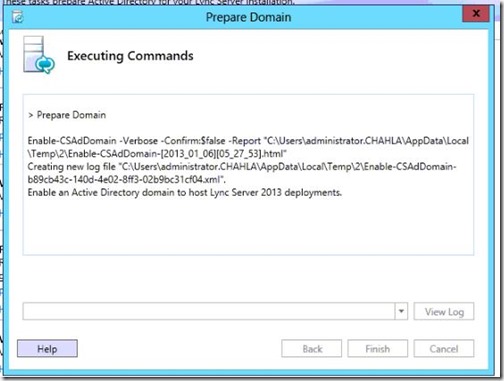
- Domain preparation finishes, click Finish.
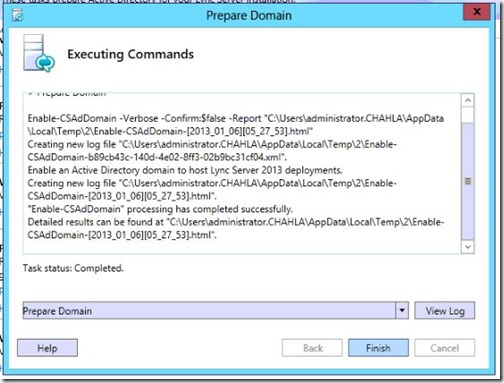
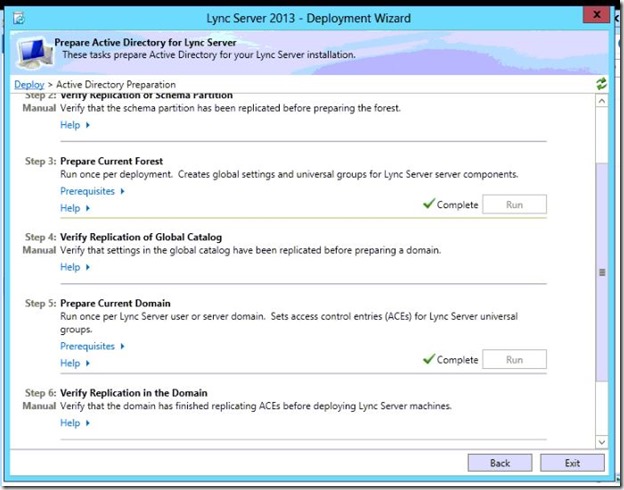
- Add users to provide administrative access
On the Domain Controller, Open Active Directory Users And Computers
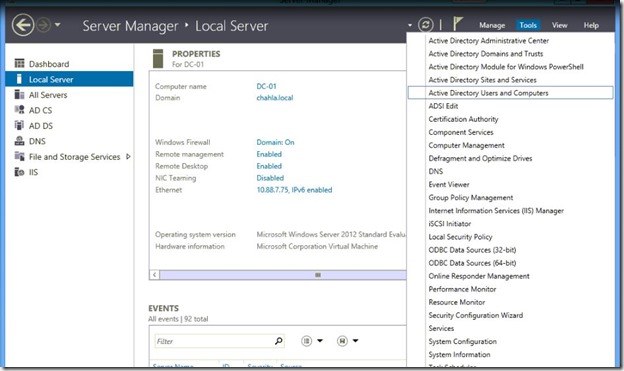
- Open the Security Group CSAdministrator and add the user who will be the Lync Administartor, i am using the Administrator account for this.

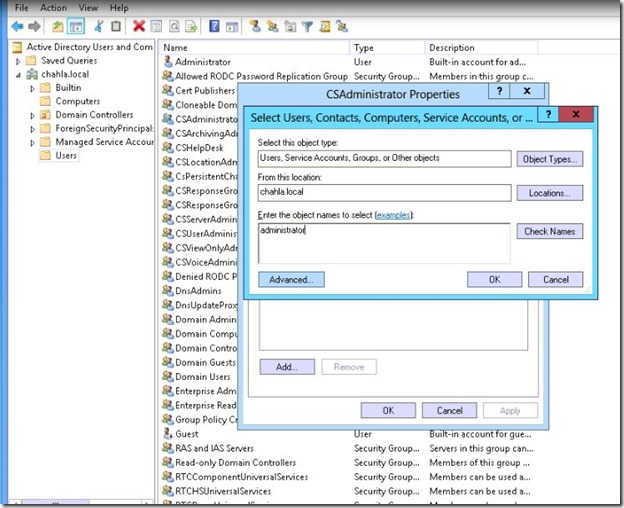
- Chahla\Administrator is now a member of CSAdministrator Group.
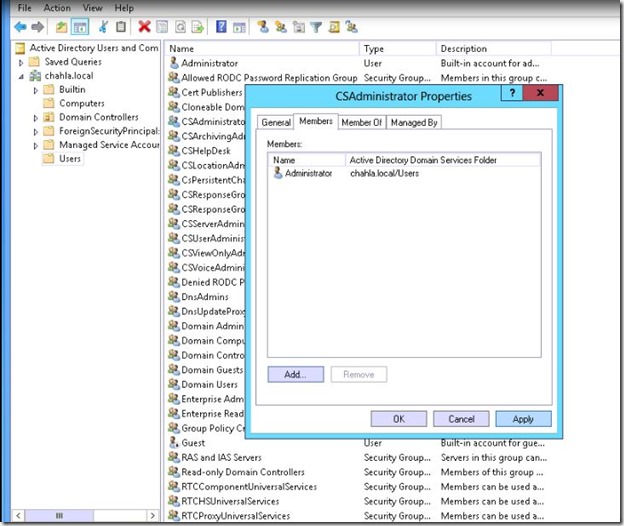
- Install RTC Instance on SQL01.chahla.local
- Open setup from the installation media.

- .Net Framework will be enabled.
- Planning page.
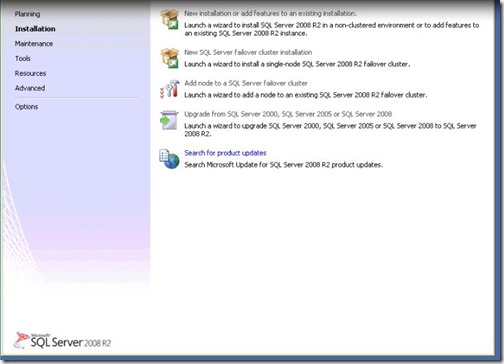
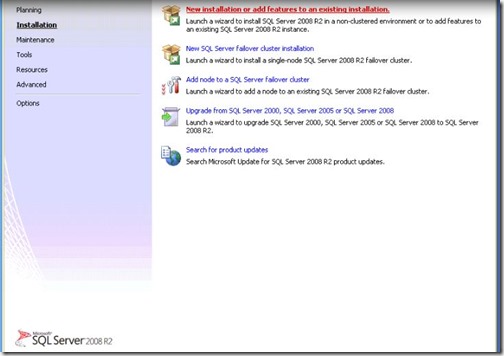
- Click on the Installation Menu, then select “New Installation or add features to an existing installation”.
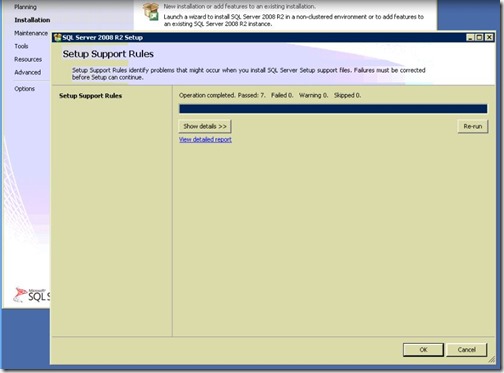
- Support files setup, click Ok.
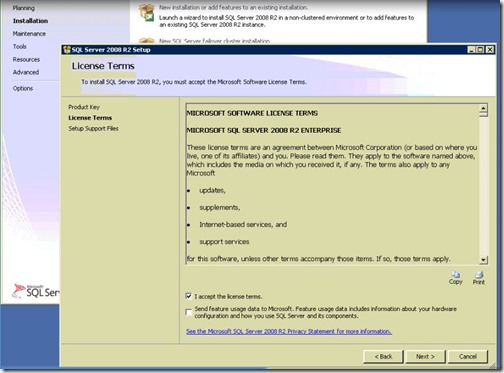
- Accept the license terms, then click Next.
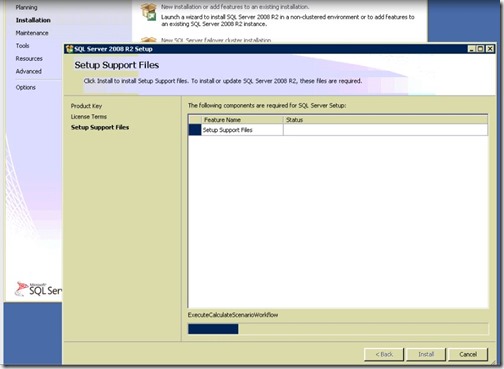
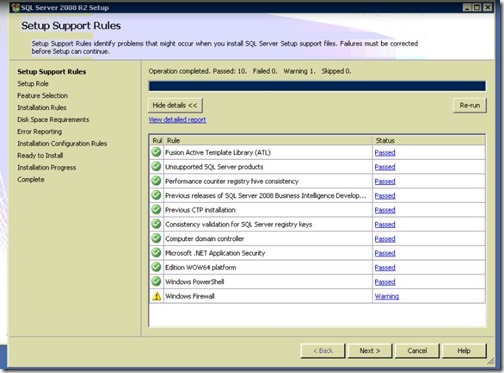
- Check if you have errors, do not proceed until you fix them, otherwise click Next.
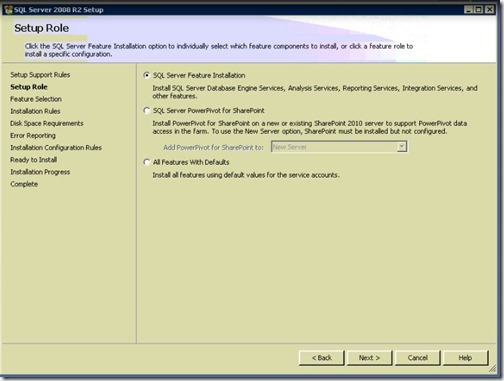
- Select SQL Server Feature Installation, then click Next.
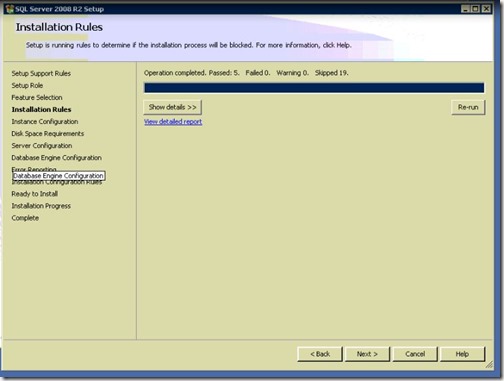
- From the list of features select “ Database Engine Services, Management Tools-Basic, Management Tools –Complete” , browse where you want to install, then click Next.

- In the Instance Configuration, select “Named Instance” and name it RTC, then click Next.

- You can create service account for this step, i created sqladmin account.
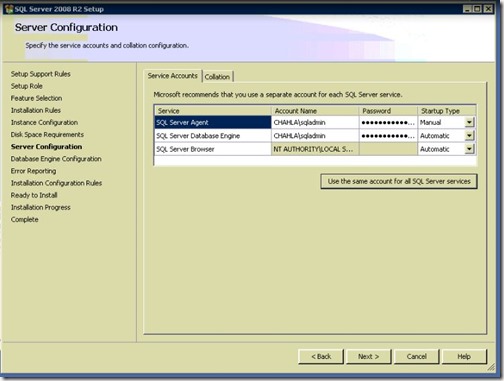
- Select Windows authentication mode, then add the users that you want to grant them unrestricted access to the Database Engine, i added Administrator and SQLAdmin, click Next.

- Click Install.

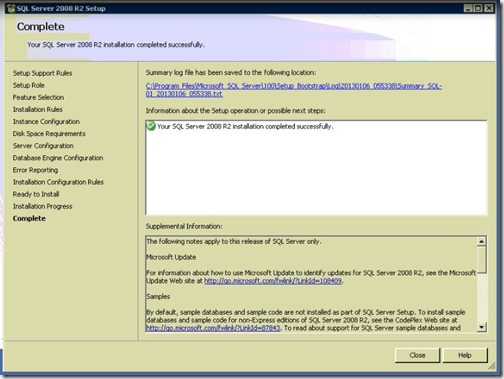
- Done.
- Install Monitoring & Archiving DB instances on SQL02.chahla.local

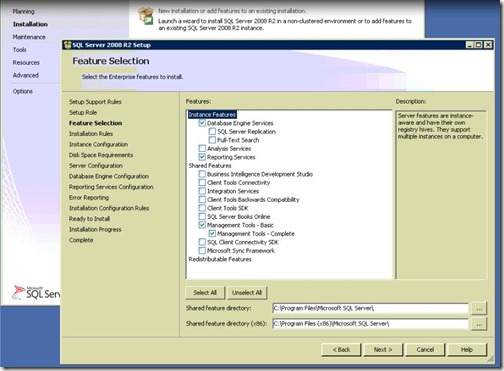
- Named Instance: LyncMonitoring (any name)

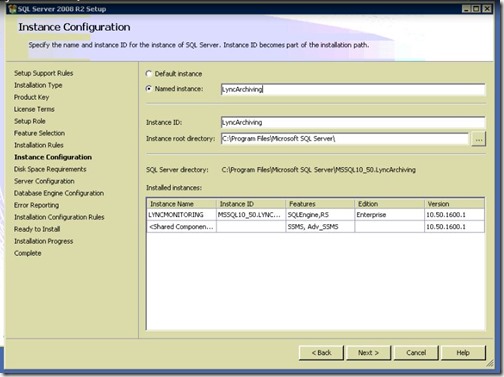
- Another new installation, Named Instance: LyncArchiving (any name)
- Now you have to allow access to some ports in each sql server
On SQL-01, open SQL Server configuration Manager.
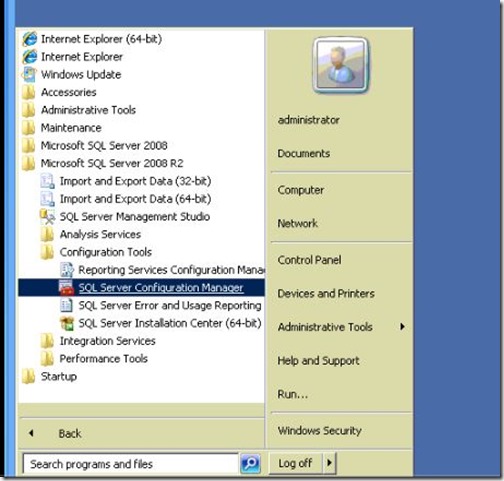
- click on Protocols for RTC, right click TCP/IP and hit Properties.
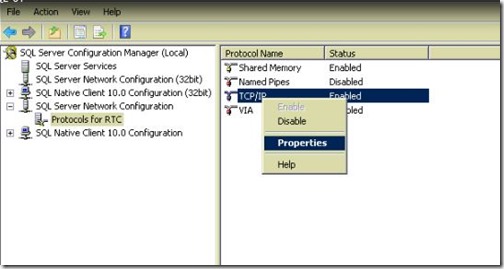
- Click on the IP Addresses tab, then at the bottom of the list you will see the TCP Dynamic Ports value used by RTC Instance. (49279 in my case)
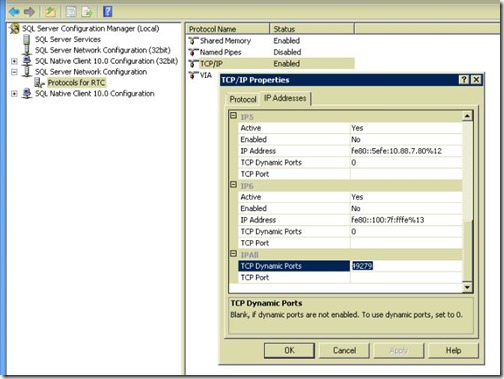
- Open Windows Firewall, and click New Rule.
- Select Port, then click Next.
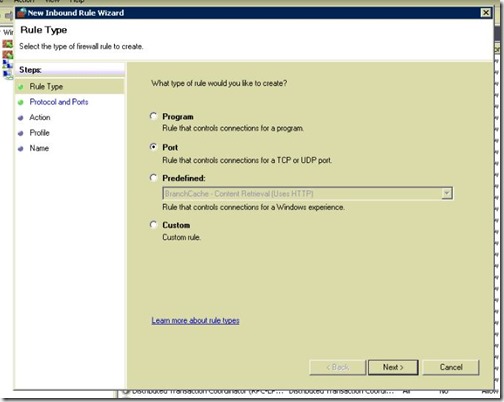
- select TCP, type the port number that you obtained in the previous step (49279), then click Next.
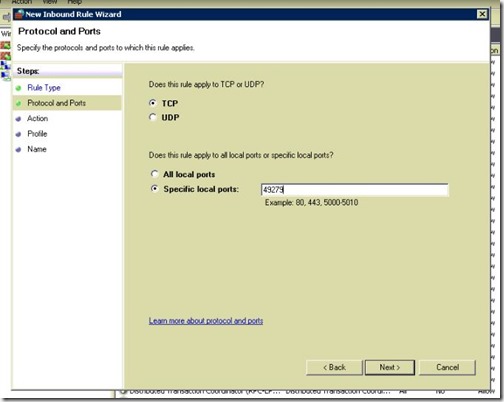
- Allow the connection, click Next.
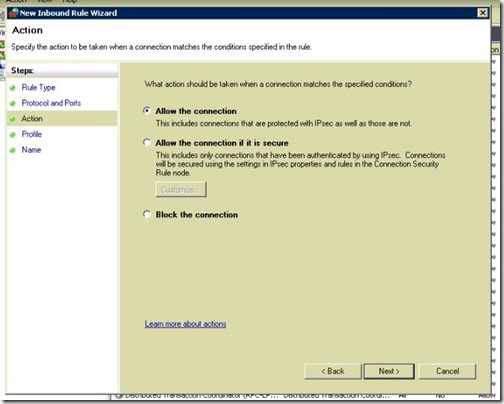
- Apply it to all profiles, click Next.
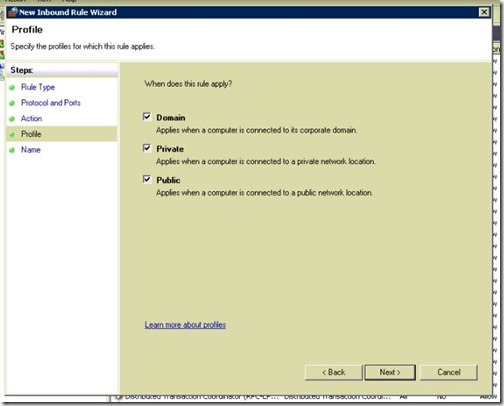
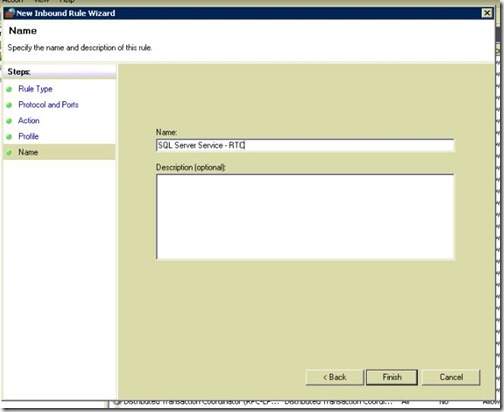
- Give it any name, then click Finish.
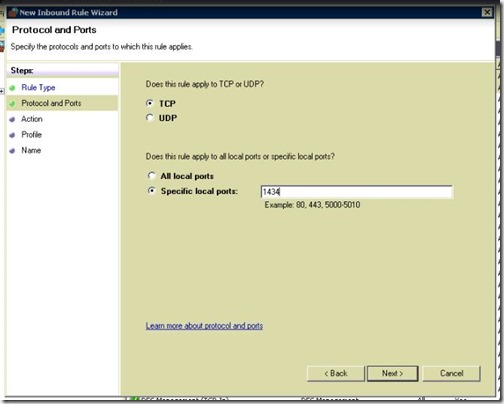
- On the same server you have to open port UDP 1434 that is used by SQL
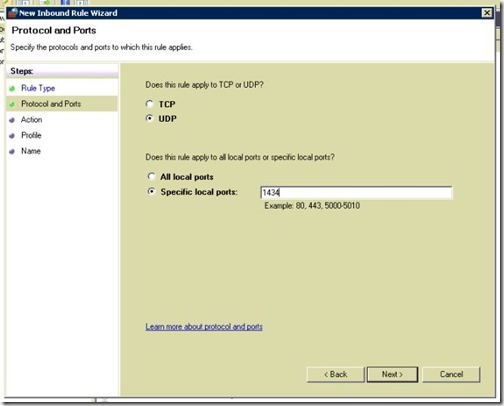
We will do the same on SQL-02 for the other two Instances (LyncMonitoring & LyncArchiving)
- for LyncMonitoring.
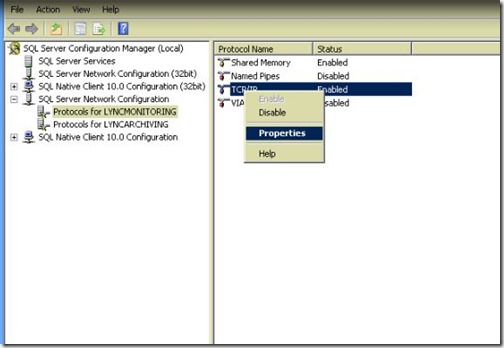
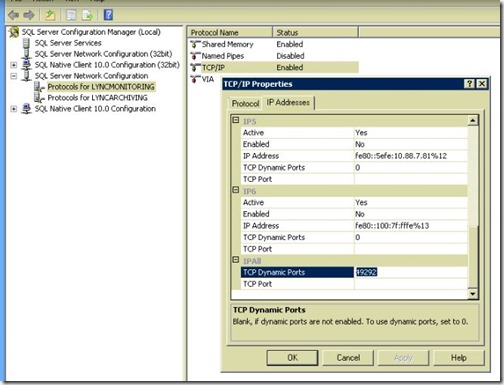
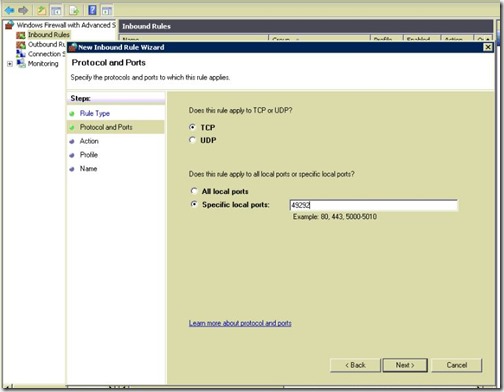
- Port is 49292 in my case.
- allow it in the firewall.
- give it a name.
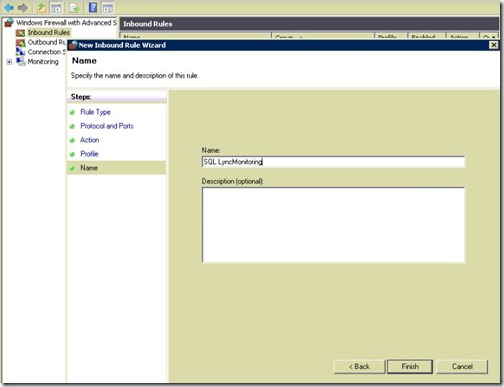
- For LyncArchiving.
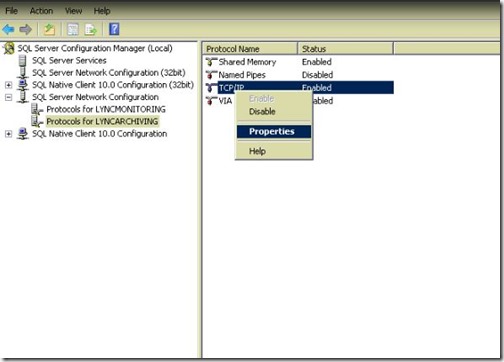
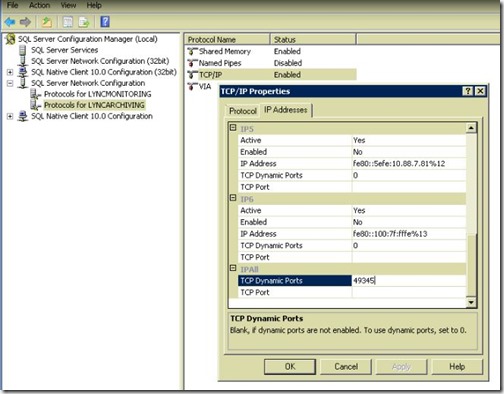
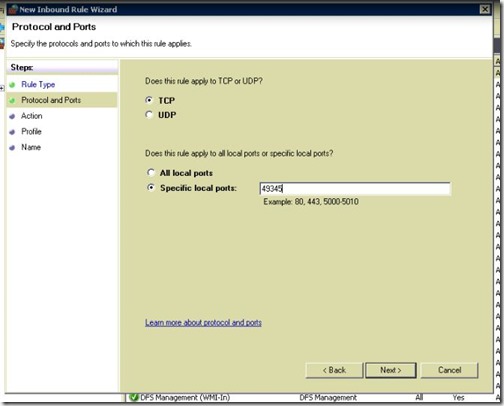
- Port is 49345 in my case.
- Allow it in the firewall.
- Give it a name.
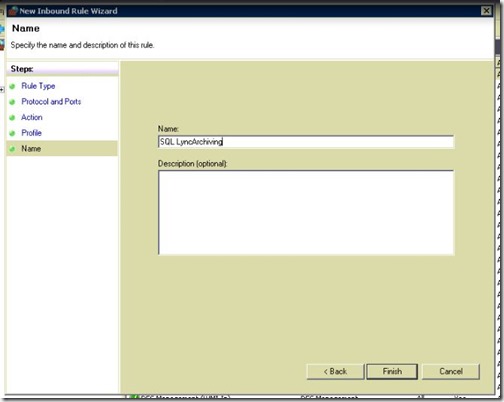
- Also don’t forget to allow UDP 1434.
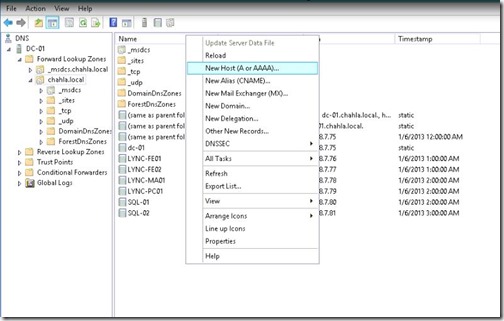
Now we will add some required DNS Records, create new Host (A or AAA)
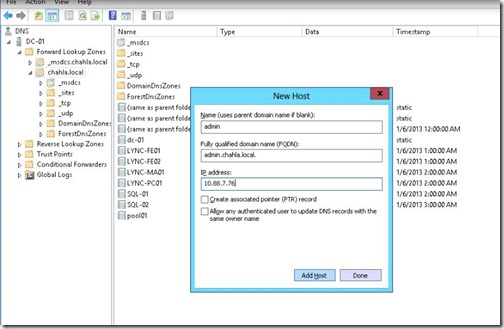
- Type the name and the IP Address of the first Front-end Server, do this for:
meet.chahla.local
admin.chahla.local
dialin.chahla.local
pool01.chahla.local
- Now we will create a Service Location record (SRV), right click and select “Other New Records…”
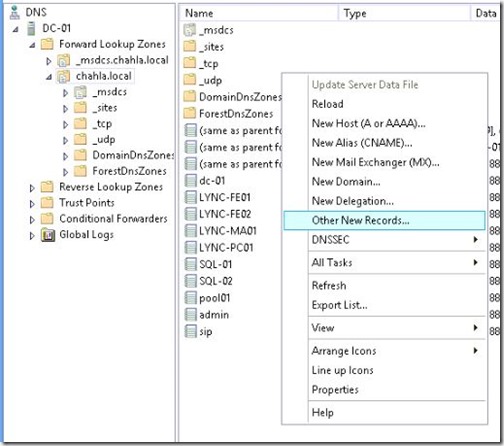
- Select Service Location (SRV).

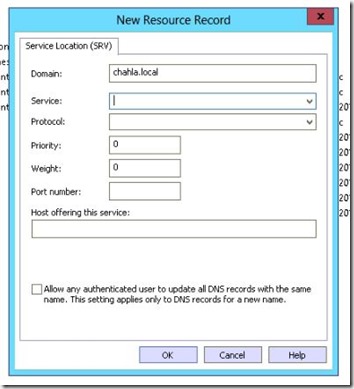
- Service: _sipinternaltls
Protocol: _tcp
Port Number: 5061
Host: pool01.chahla.local
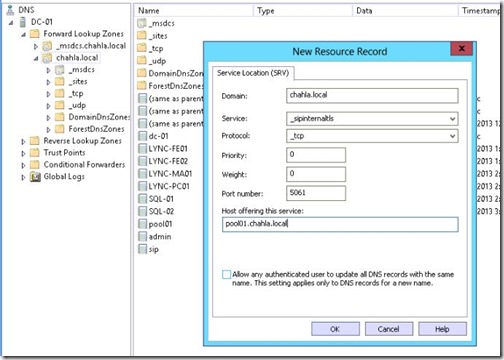
- The Next step is to create Lync File Share
i will create mine on DC-01.chahla.local
- Share the folder.
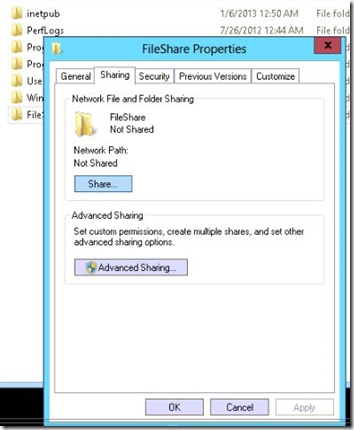
- Give Everyone (Read) permission level, and the RTCComponentUniversalServices, RTCHSUniversalServices, RTCUniversalConfigReplicator, RTCUinversalServerAdmins (Read,Write) permission level.

- Back to the first Front End server, lync-fe01.chahla.local.
Open the Deployment Wizard, then click Install Administrative Tools.


- Next, we will create the Topology, open Lync Server Topology Builder.
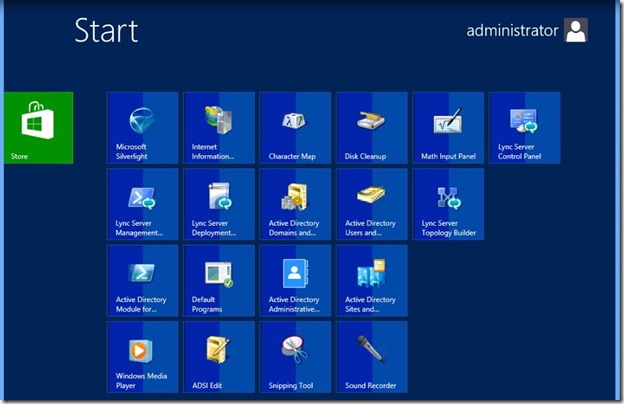
- Select New topology, then click OK.
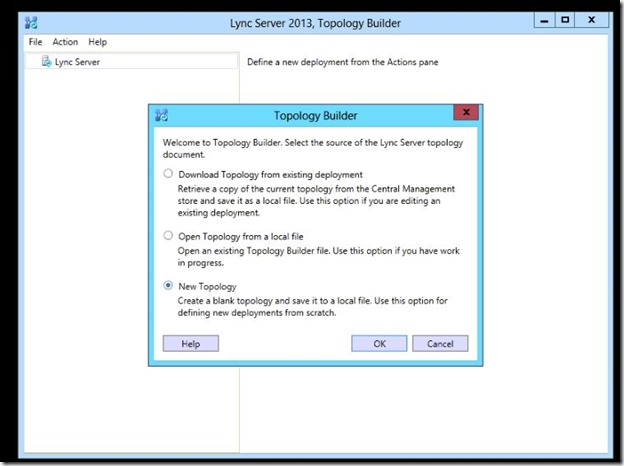
- Browse to the directory that you want to save the tbxml file, give it a name then click Save.
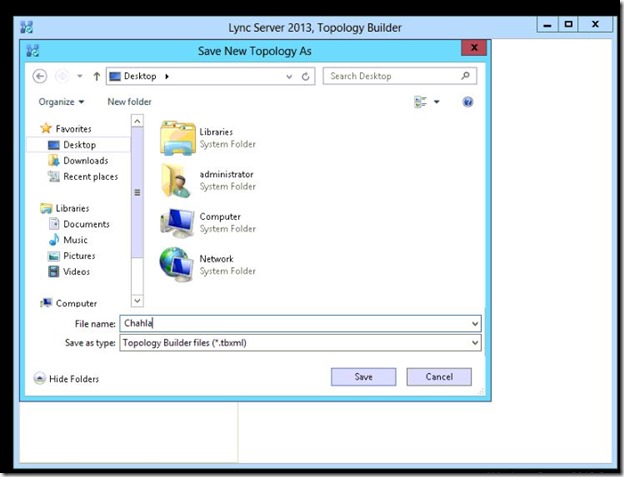
- The Create New Topology starts, click Next.
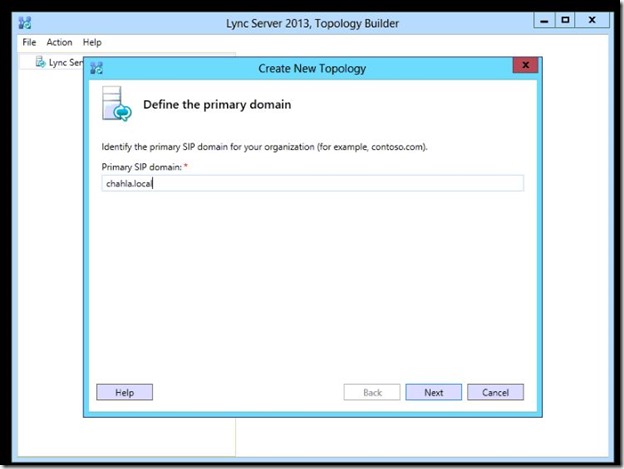
- On the “Specify additional supported domains” click Next.
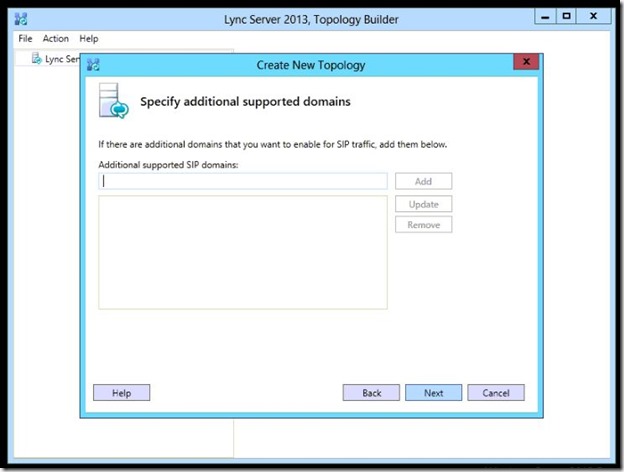
- On the “Define the first site” page, type the name and the description of your first site then click Next.
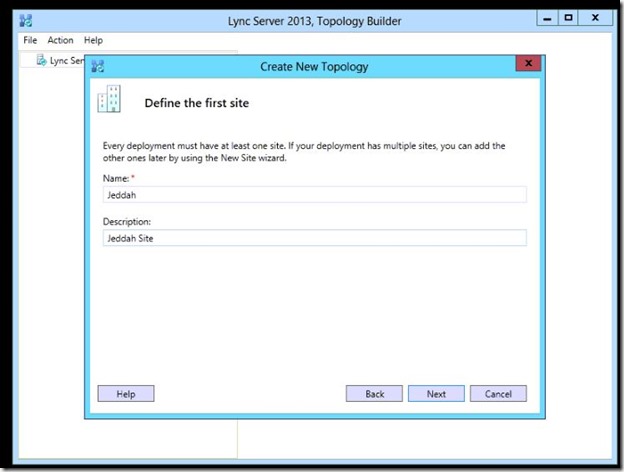
- Specify site details, then click Next.
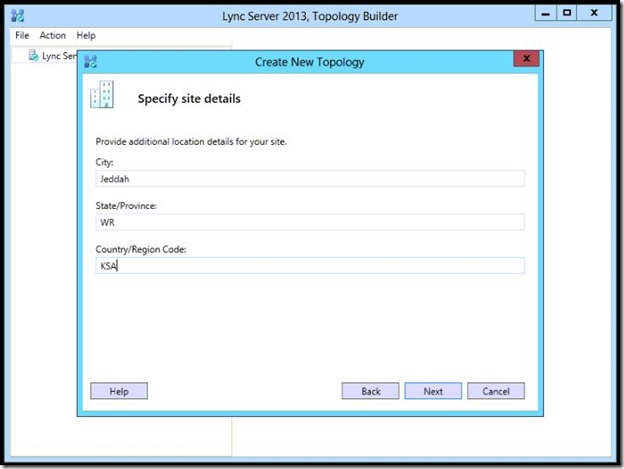
- At the last page of defining your topology, make sure the “Open the new Front-End Wizard” is checked, then click Next.
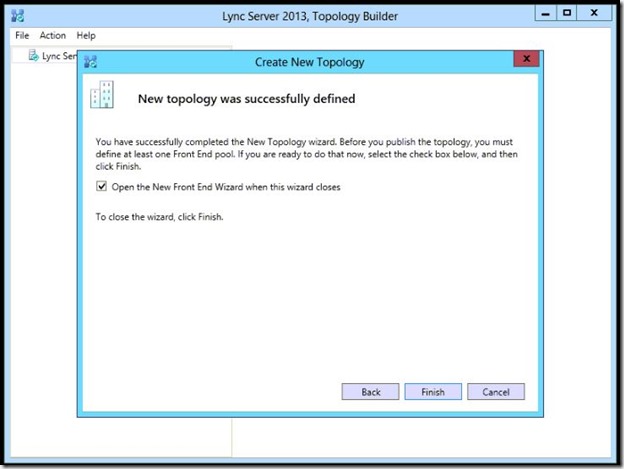
- Front End pool wizard starts, click Next.
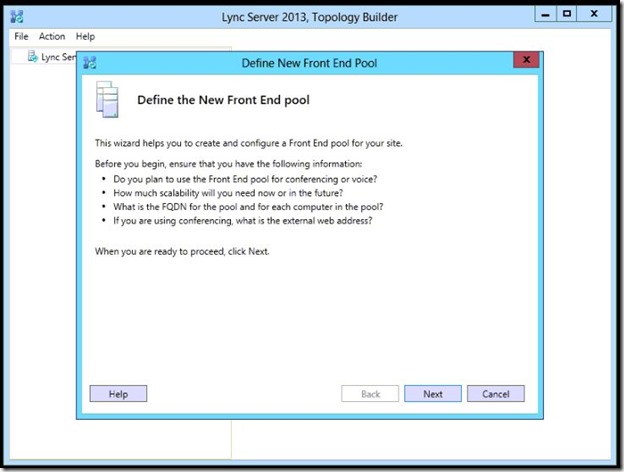
- Select “Enterprise Edition Fron End Pool”, type the Pool FQDN then click Next.
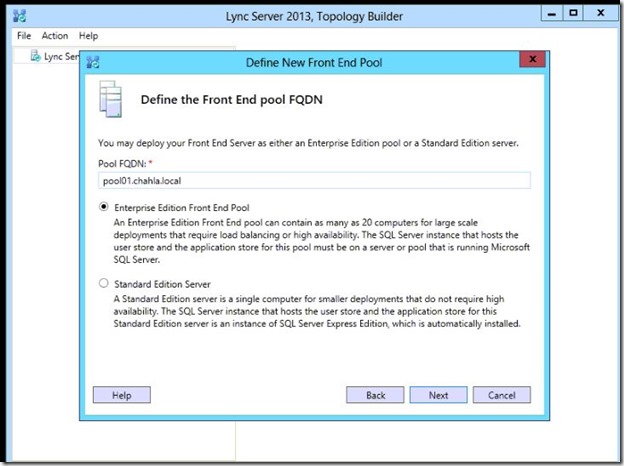
- At this step, add your FE servers then click Next.
- Select the features that you want to enable then click Next. (i selected Archiving and Monitoring because i will be using later on)

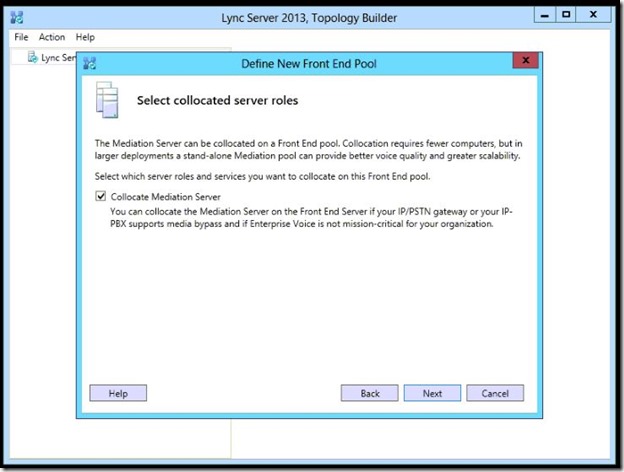
- If you will use an Edge server, this is where you should define it.
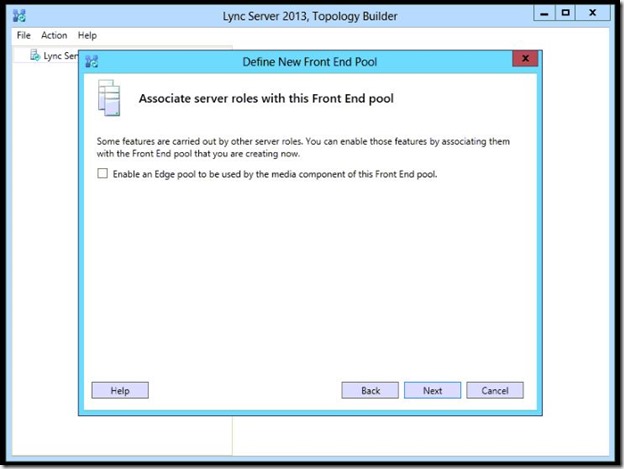
- Click “New” to define a new SQL server store.
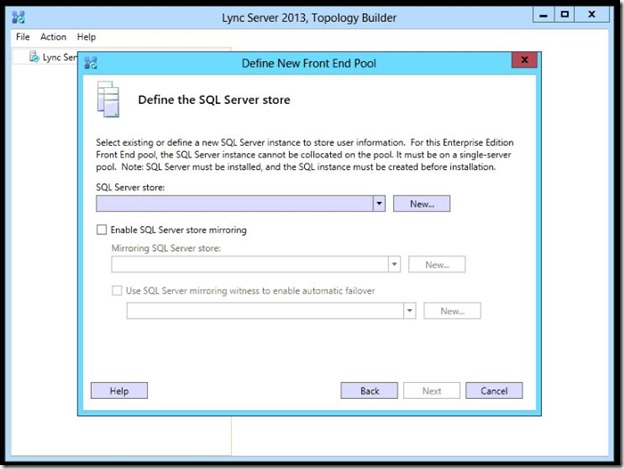
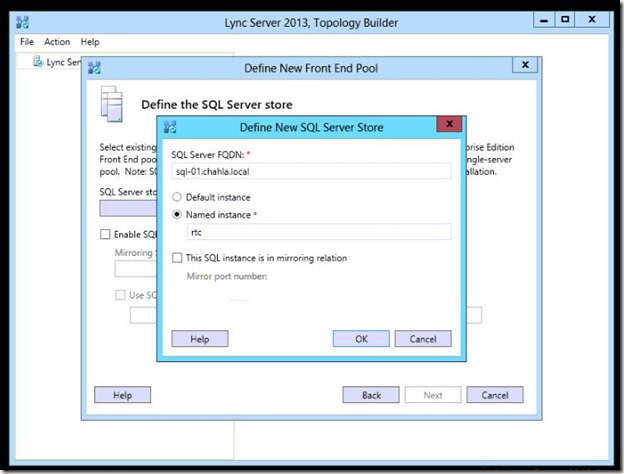
- Type the Server FQDN and the Name of the instance then click Ok.
- Click next.
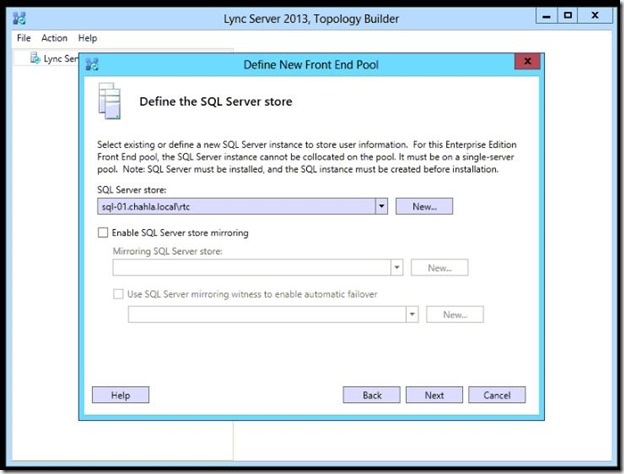
- Now define the File store that you created and shared before.
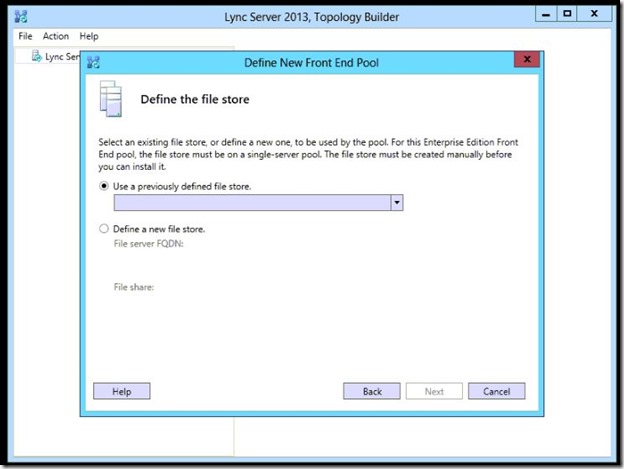
- Select “Define a new file store”, type the FQDN of the server holding that shared folder, and the name of the folder then click Next.
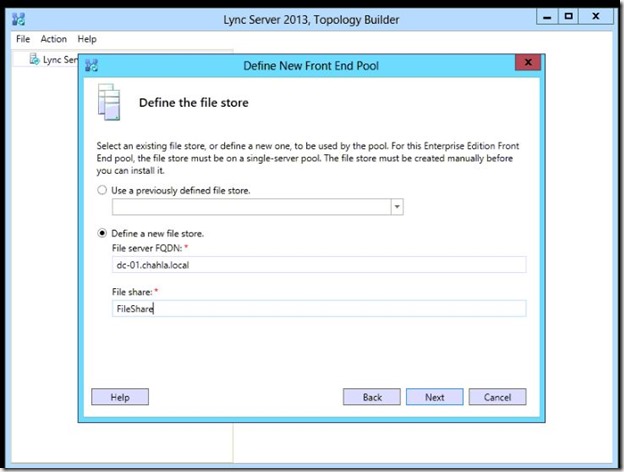
- Here you can specify the External URL for the Web Services, i am not going to use it externally, so i will keep it as is.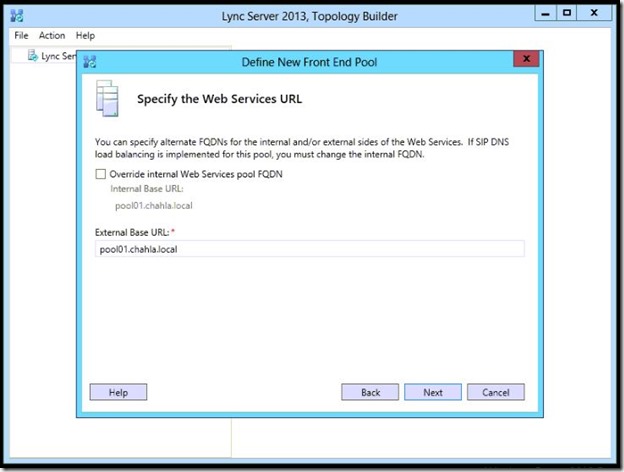
- This step to define an Office Web Apps Server if you have one.
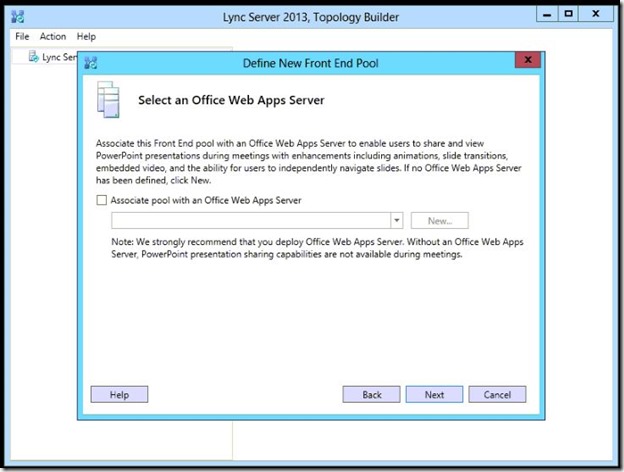
- Next, i will define a new Archiving and Monitoring Store for later on use.
Select New.
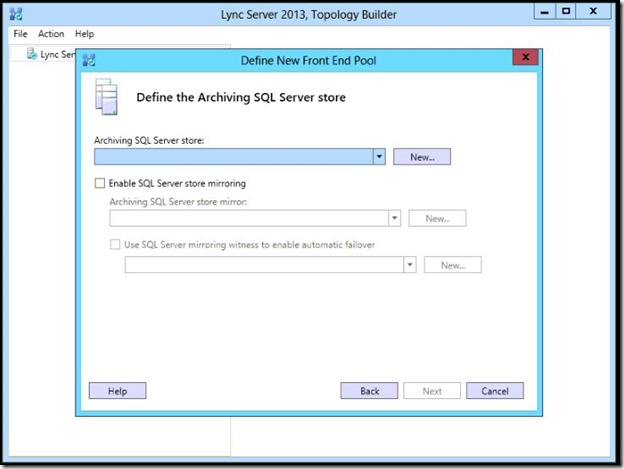
- Type the SQL Server FQDN, Select “Named Instance”, type the name of the instance and click OK. (if you are mirroring your instance you can check that option and type the port number there”
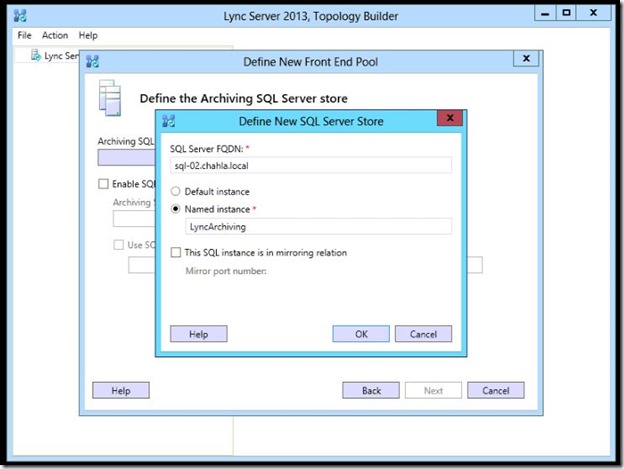
- the archiving store appears, click Next.
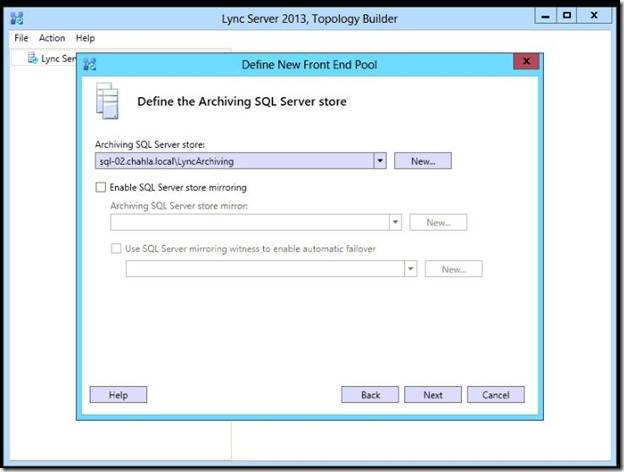
- The same thing for Monitoring, New store.
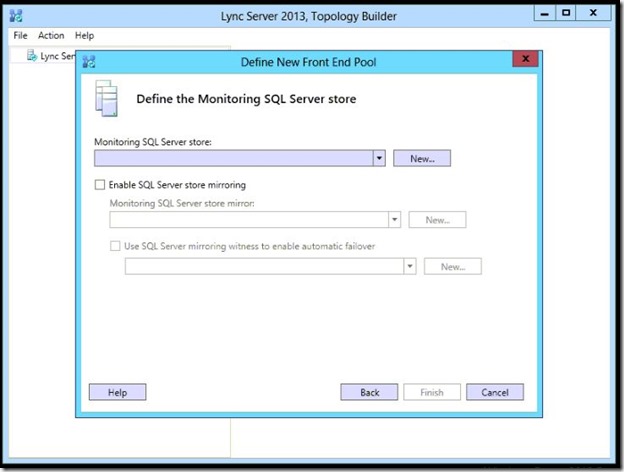
- Server FQDN and Instance Name.
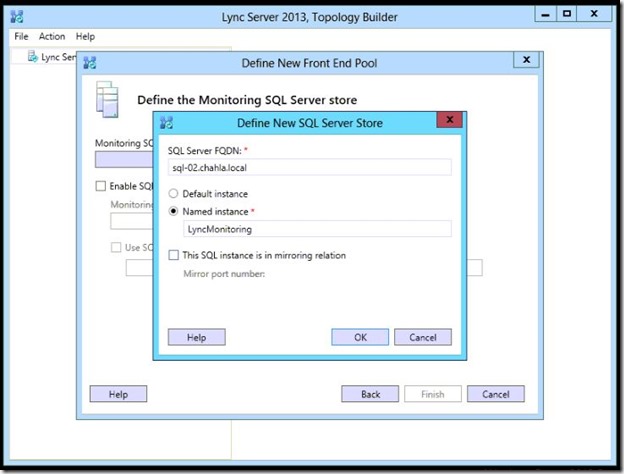
- Store appears, click Finish.
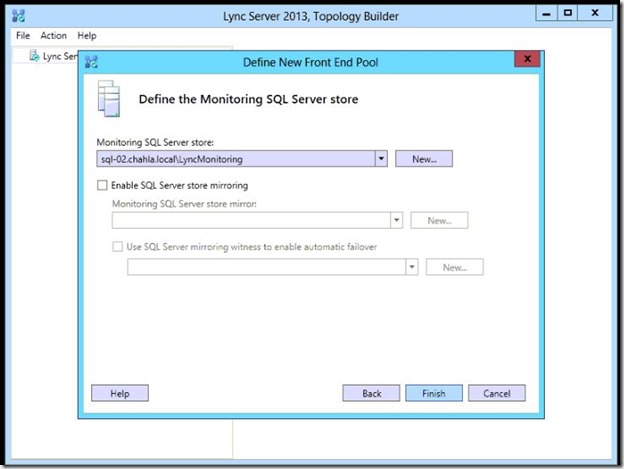
- After you finished the wizard you need to edit the Administration URL.
- Right Click to edit the properties of your topology, click Edit Properties.
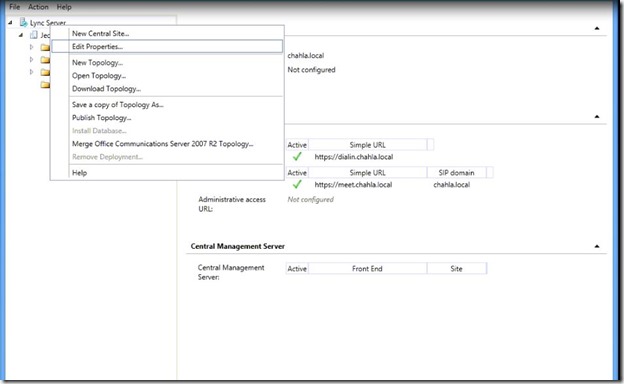
- Click “Simple URLs”
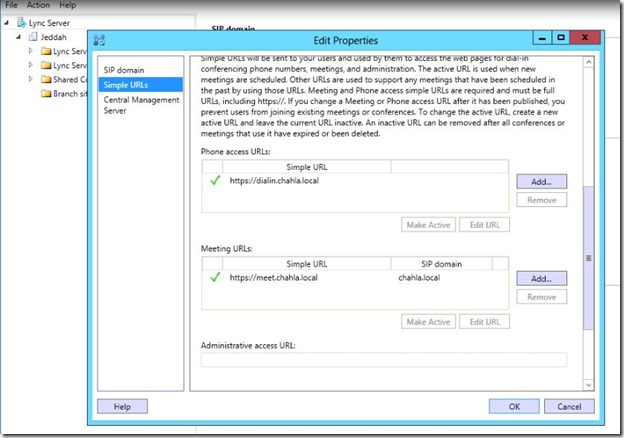
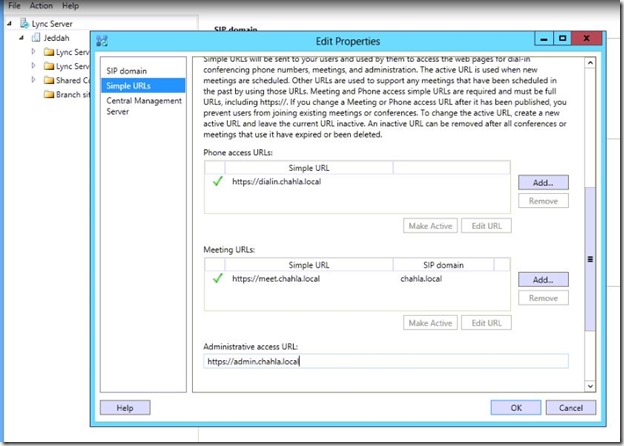
- in the “Administrative access URL” type the admin URL (https://admin.chahla.local in my case) and click OK.
- Then Publish the Topology.
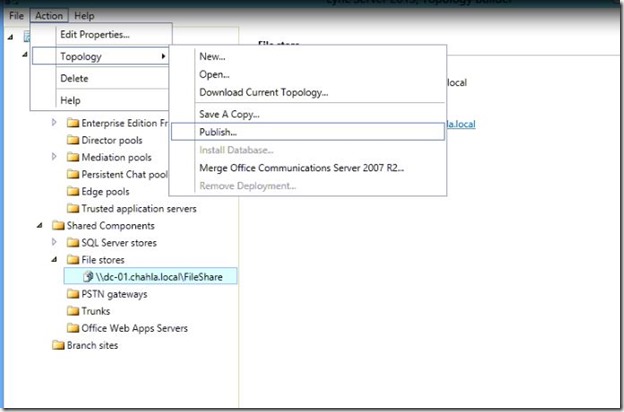
- Click Next.
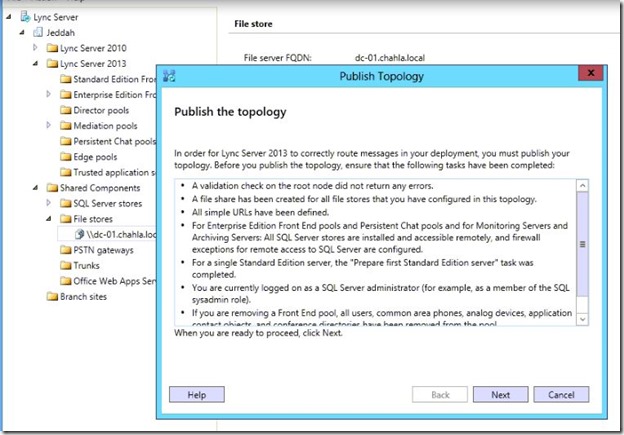
- Click Next.
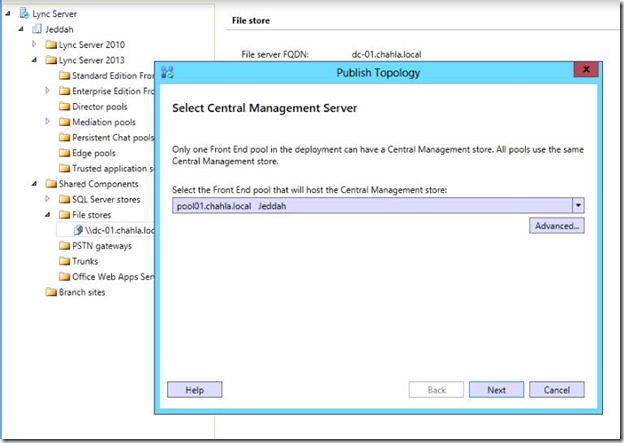
- Click Next.

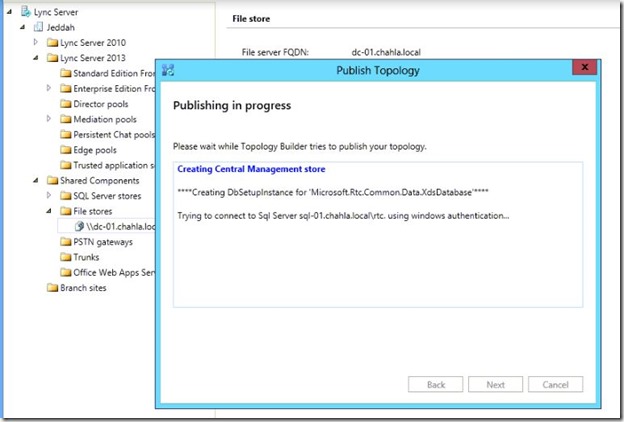
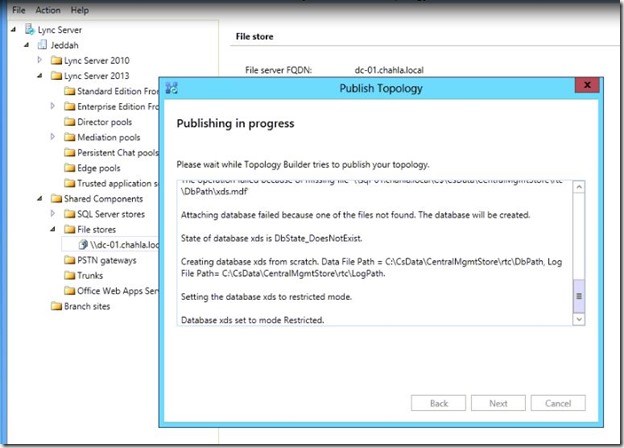



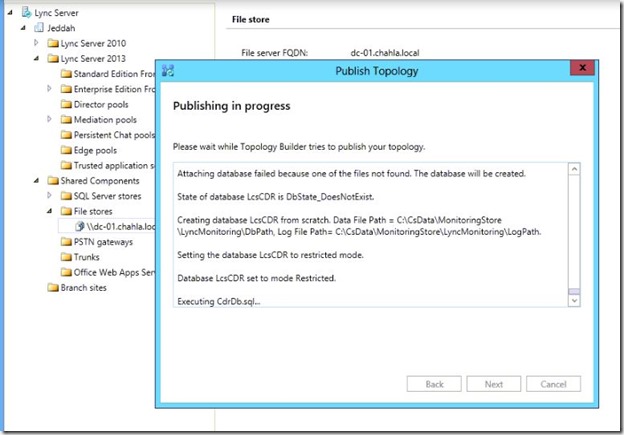
- Succeeded with warning, we will see the warning details.

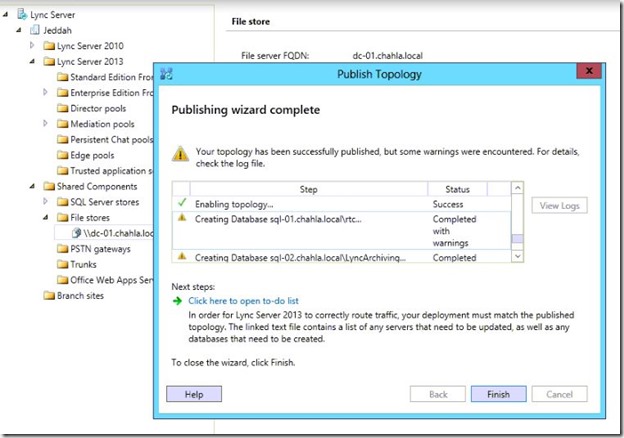
- the warnings are because of the default settings of SQL Server, you can simply ignore it.


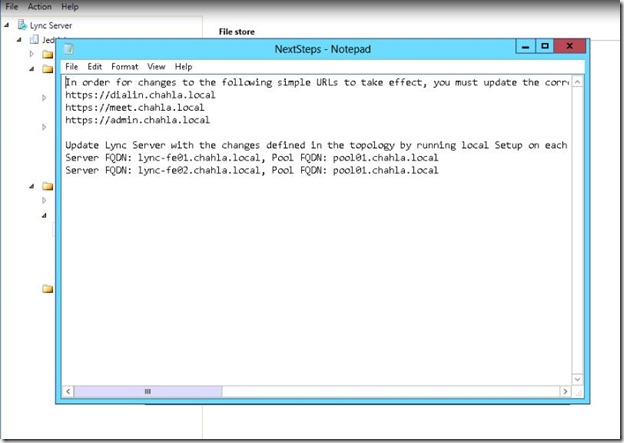
- Next step is to Install Local Configuration Store & Lync Server Components on Lync-FE01
Open the Deployment Wizard, and click “Install or Update Lync Server System”
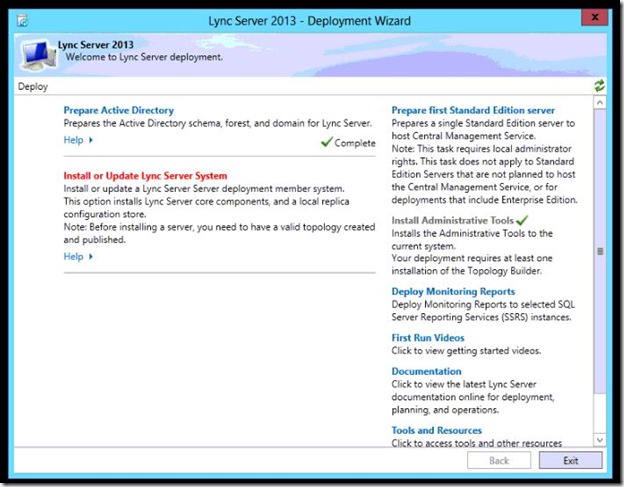
- On the right side of Step 1 click Run.
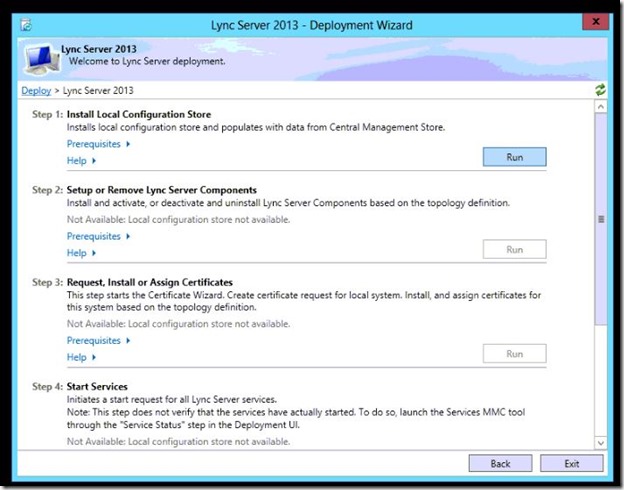
- Select “Retrieve directly from the CMS,,,,” then click Next.


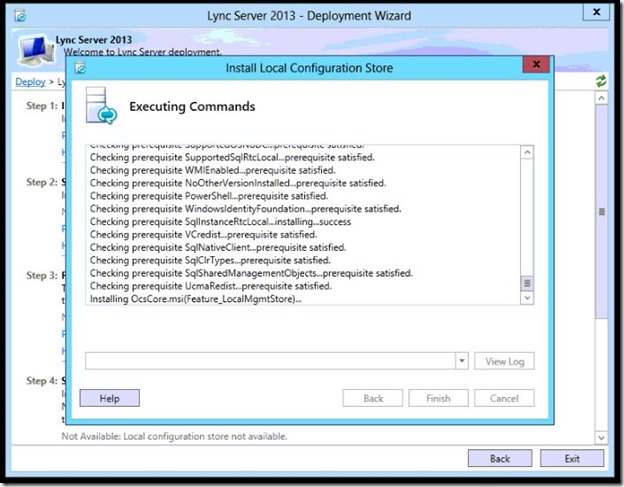
- Step 1 completed, click Finish.
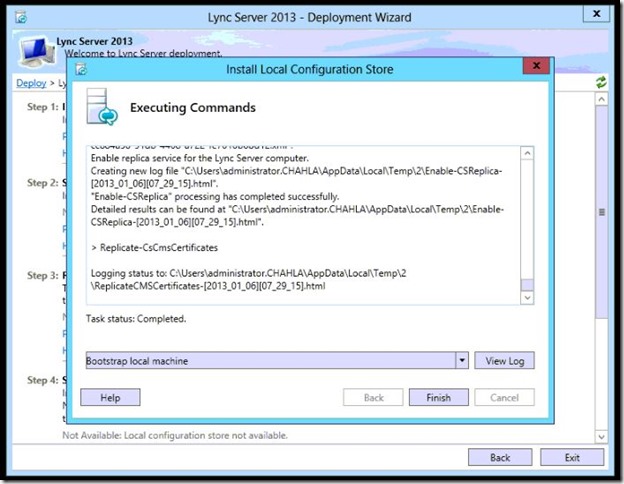
- Step 2, Run.

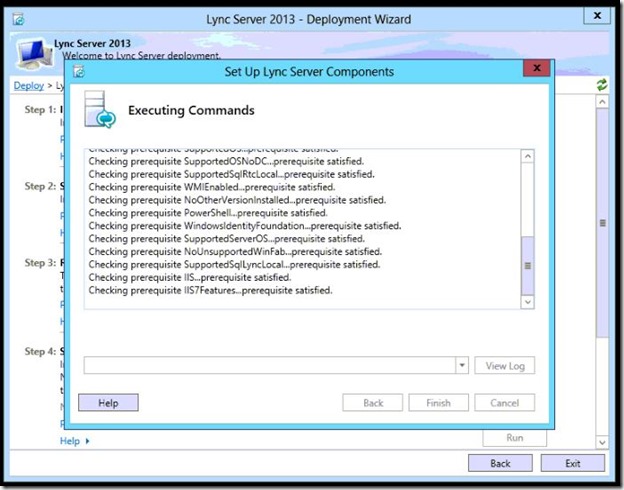
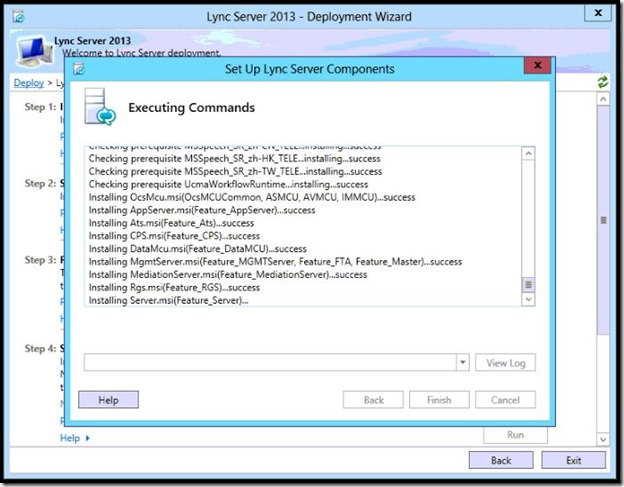
- Step 2 completed, click Finish.
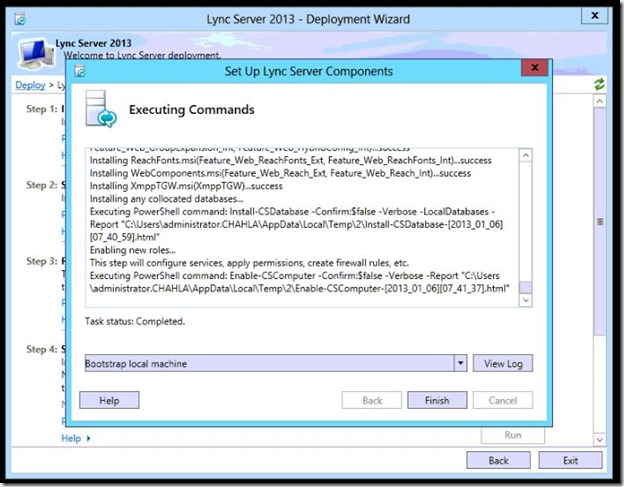
- Now we need to Request And Assign Certificate, Step 3 click Run.
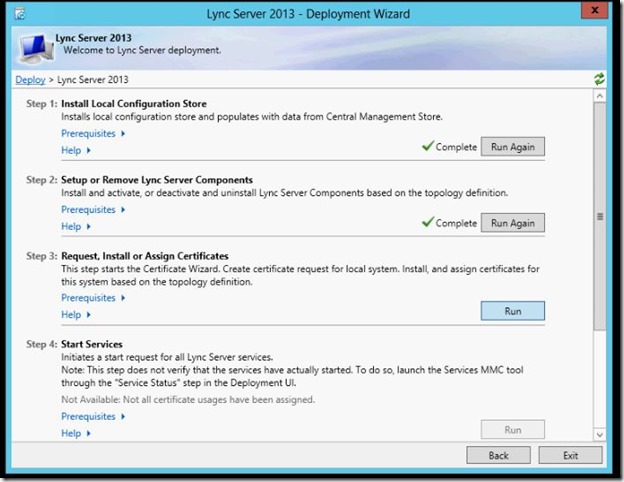
- Click Request.

- Select “Send the request immediately to an online certification authority”
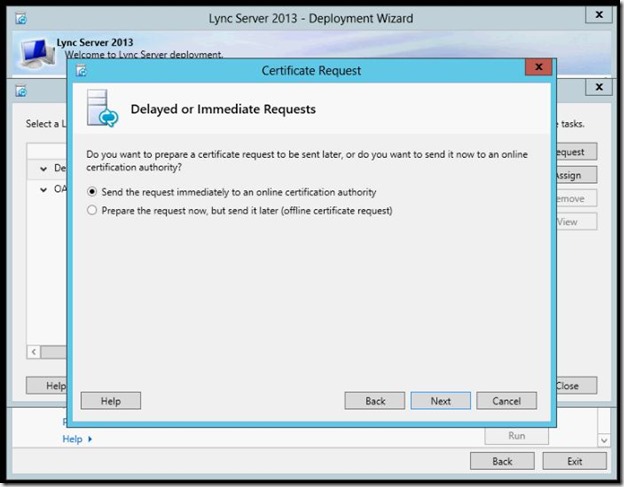
- Select your CA.
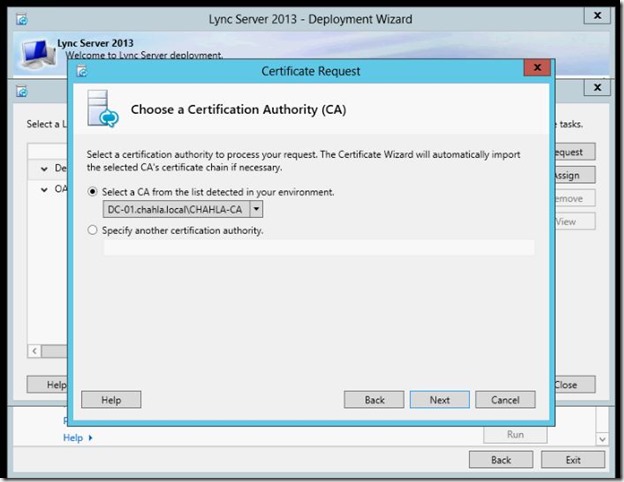
- click Next.
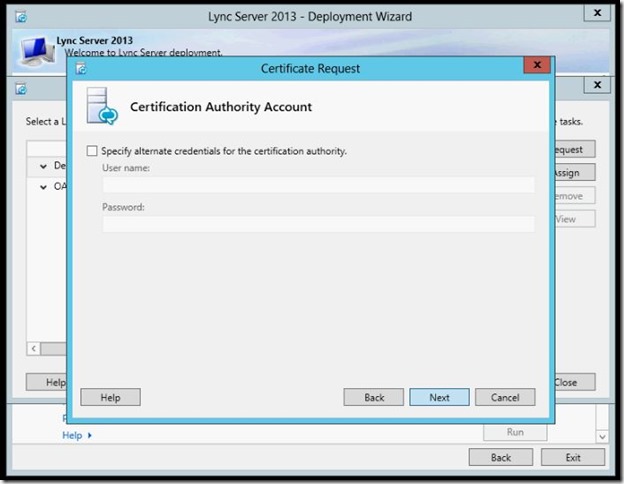
- click Next.
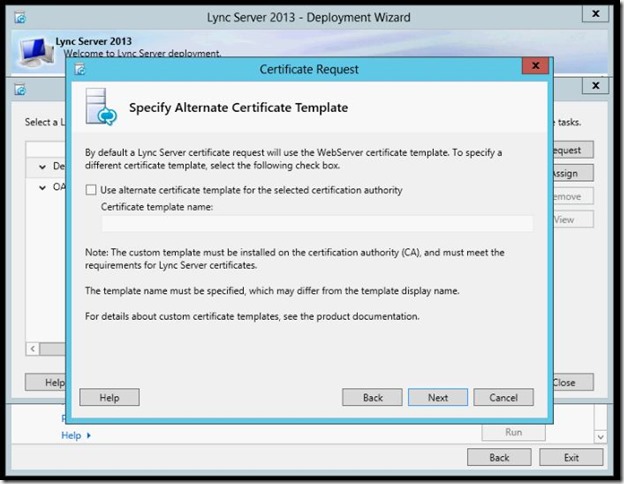
- type a Name for your Certificate, select the Bit Length and click Next.
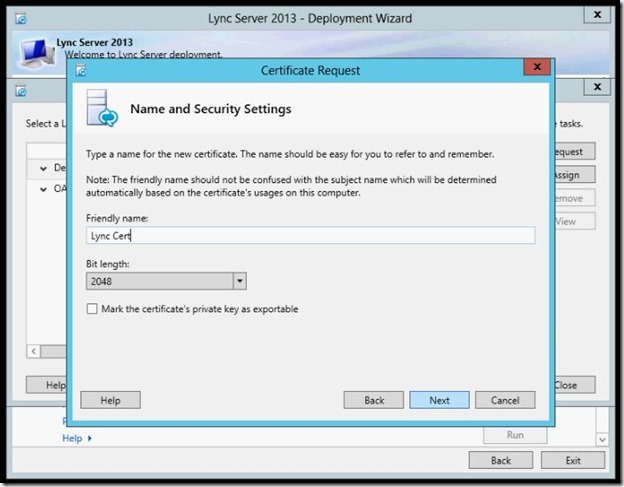
- Fill in the Organization name and unit then click Next.
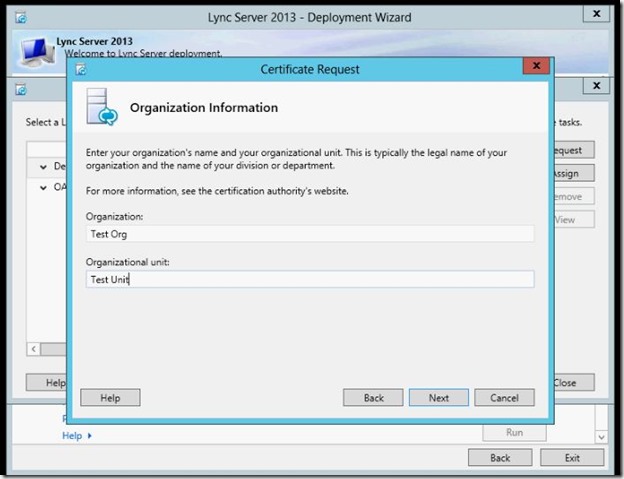
- Fill in the Geographical info and click Next.

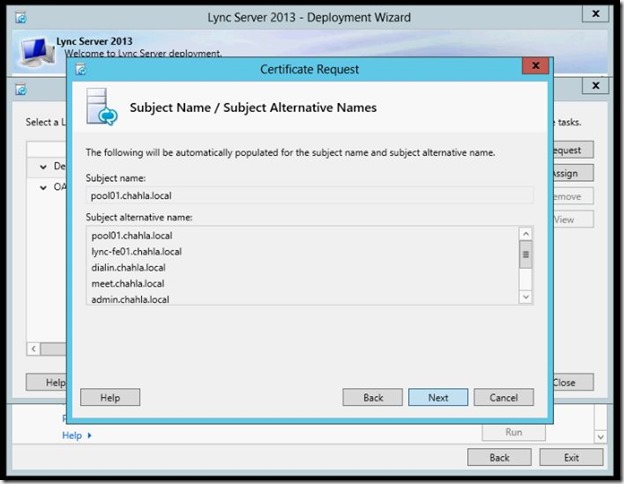
- Select your sip domain, then click Next.
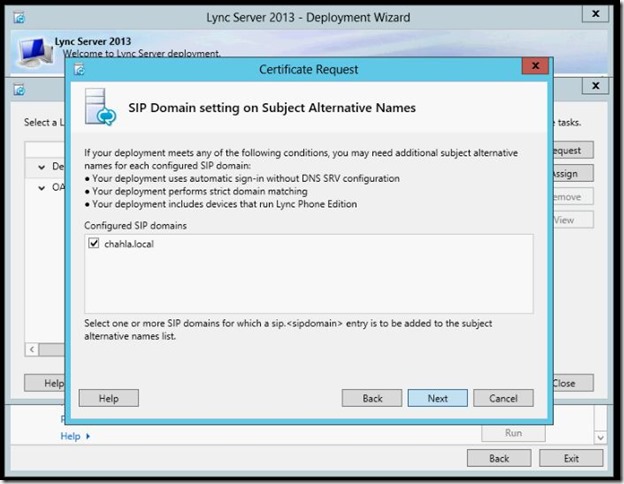
- Here you can add additional Subject Alternative Names.
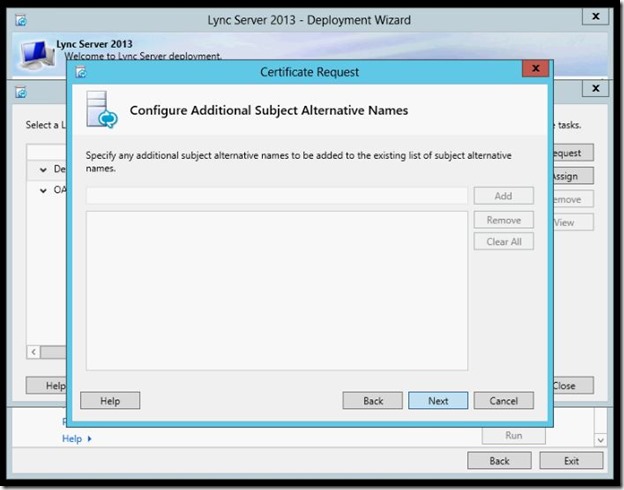
- the request is completed, click Next.
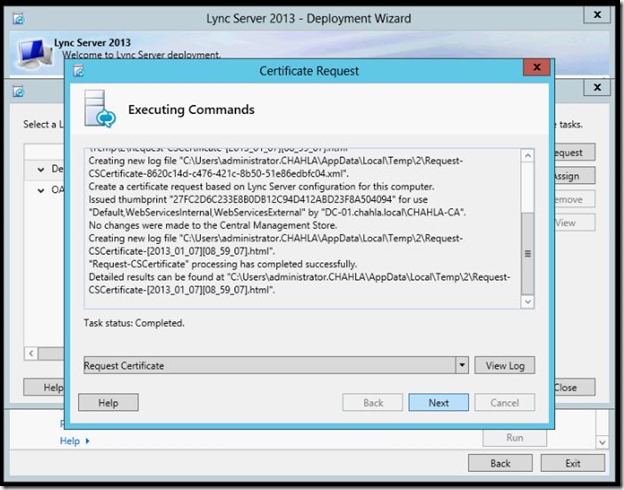
- Make sure the “Assign this certificate to lync Server ,,,,” is checked then click Next.



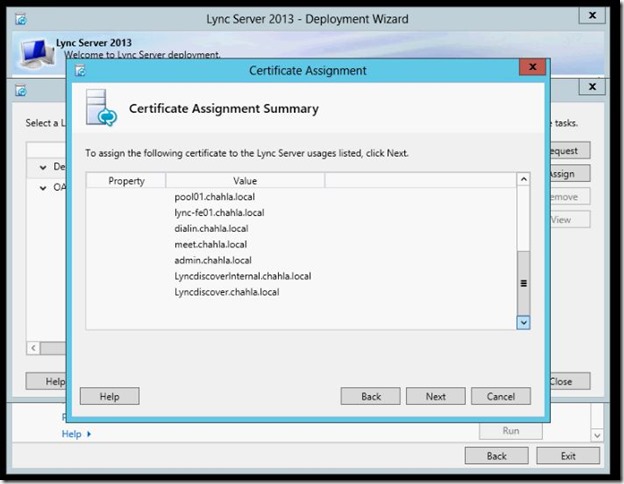
- Certificate Assignment is completed, click Finish.

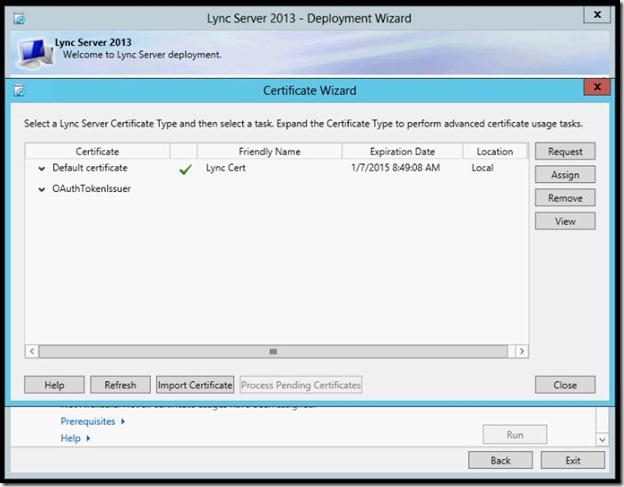
- Open your browser and type the admin url or pool url then /cscp , type your credentials and hit OK.
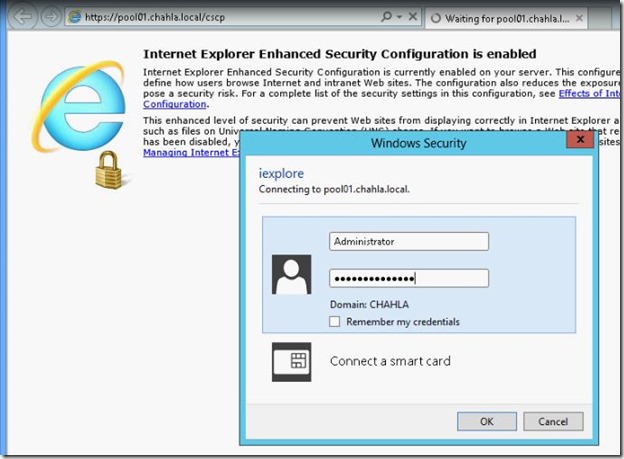
- You are done with the first FE server.
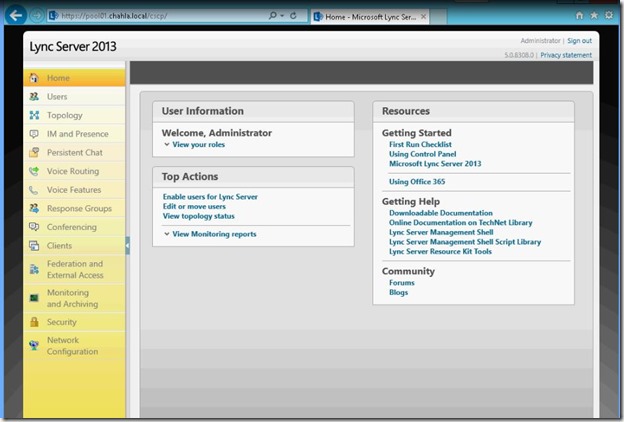
- Install Second Front End Lync-FE02.chahla.local (make sure you install the prerequisites same as FE01)
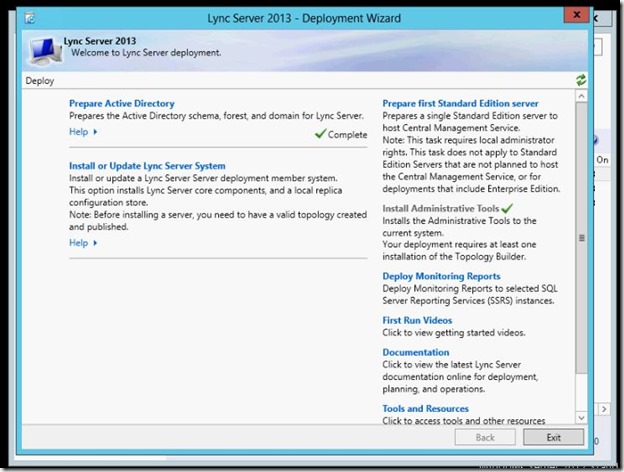
- Install Local Configuration Store, then Lync Server Components.
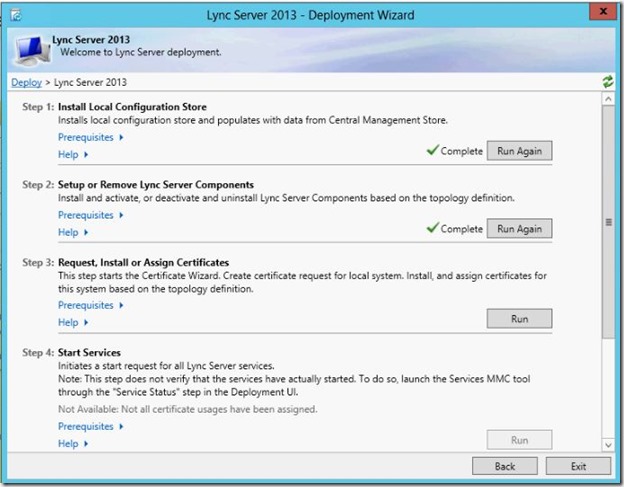
- Then request or import a certificate. (you can import the certificate that you created for FE01 if you added the name of the second front end server in the certificate SAN and if you checked the option to make the key as exportable")
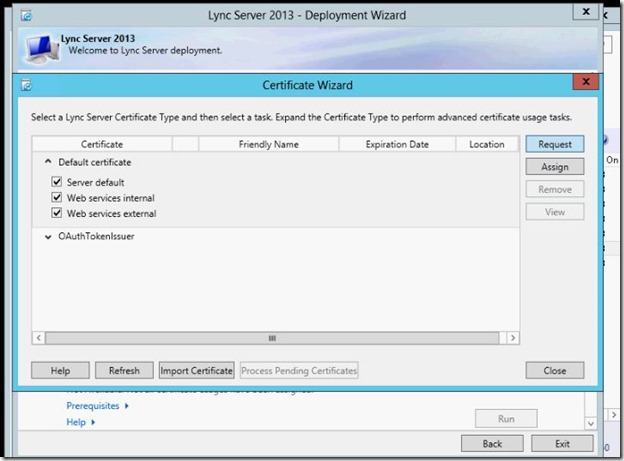
- Request a certificate.
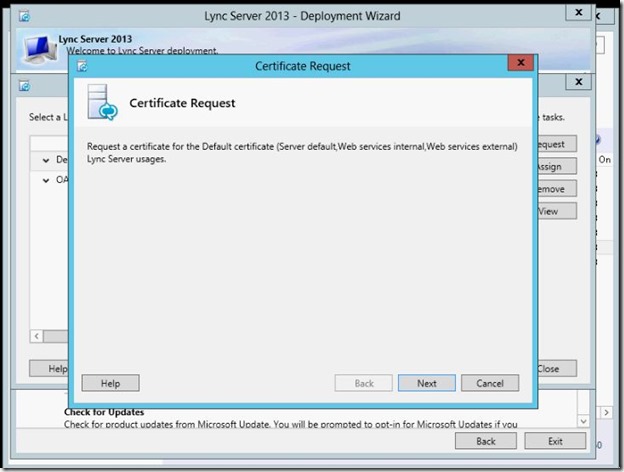


- Make sure you check the option “ Mark the certificate’s private key as exportable”, type the name then click Next.




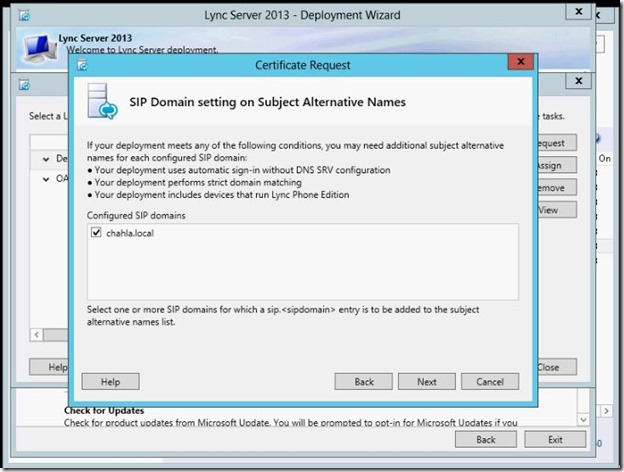
- Add the second FE server.
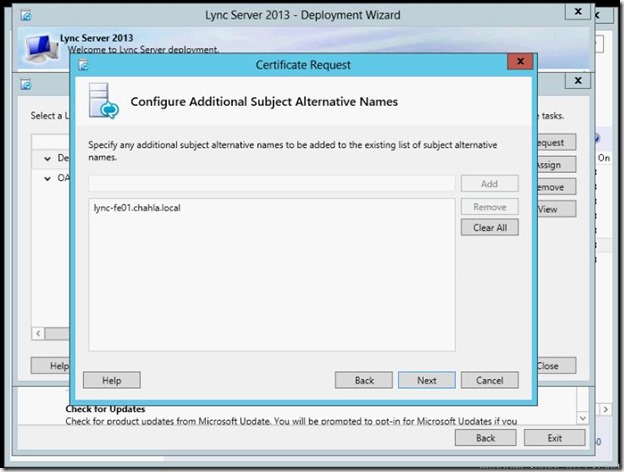
- Make sure both servers are listed, then click Next.
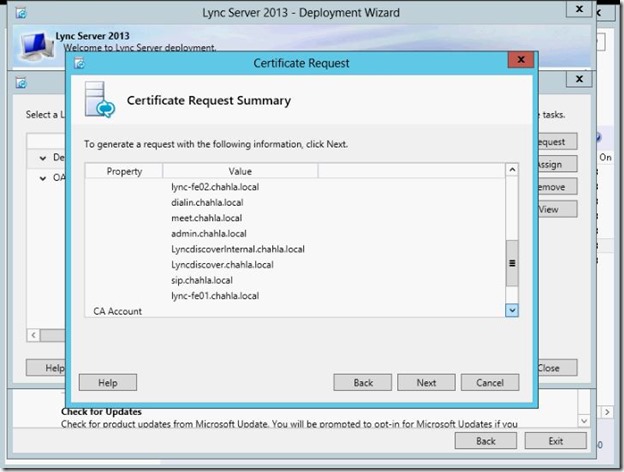
- Certificate Request is done, click Next.
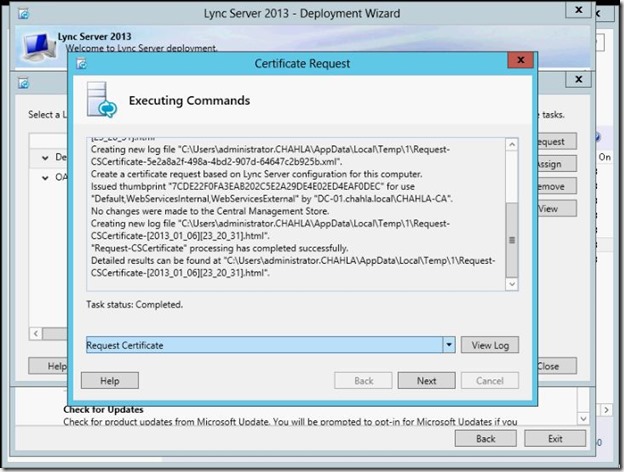
- Make sure “Assign this certificate to Lync Server …..” then click Finish.
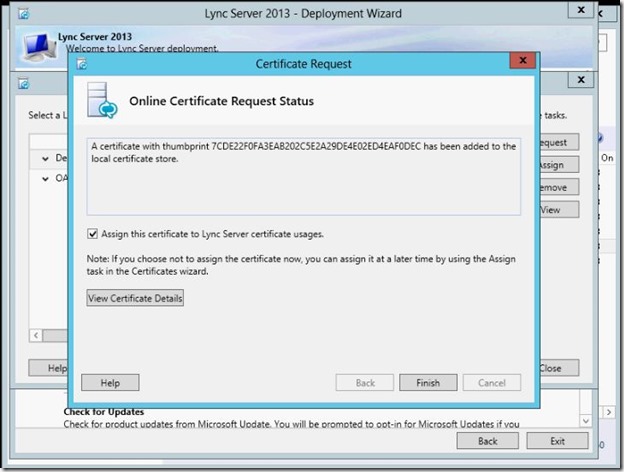
- Certificate Assignment wizard opens.
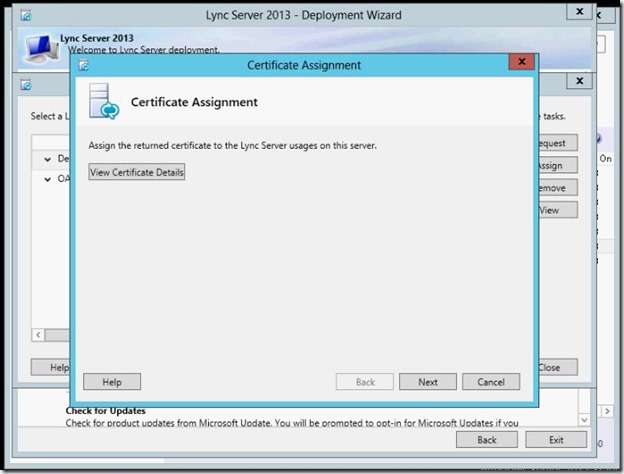
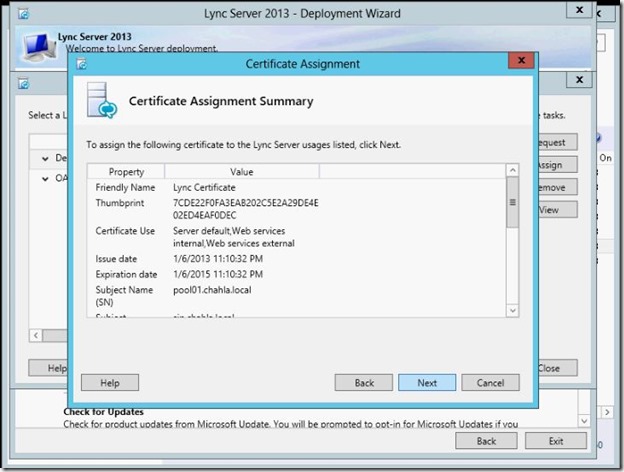
- Assignment is ok, click Finish.
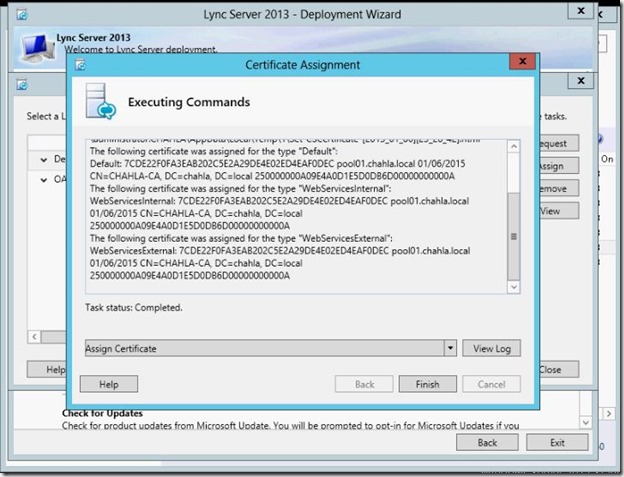
- Select OAuthTokenIssuer then click Assign.
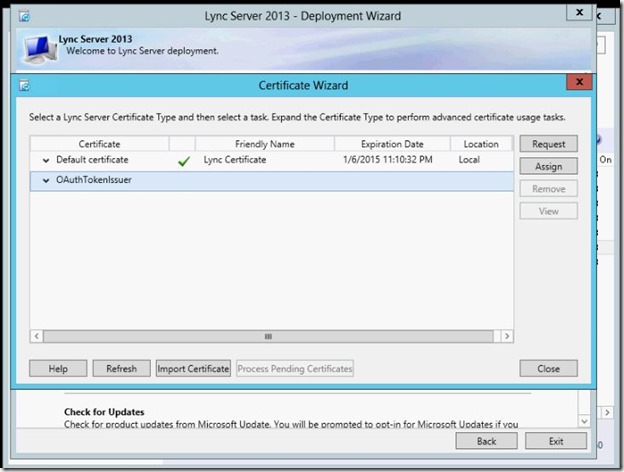
- Click Next to Assign.
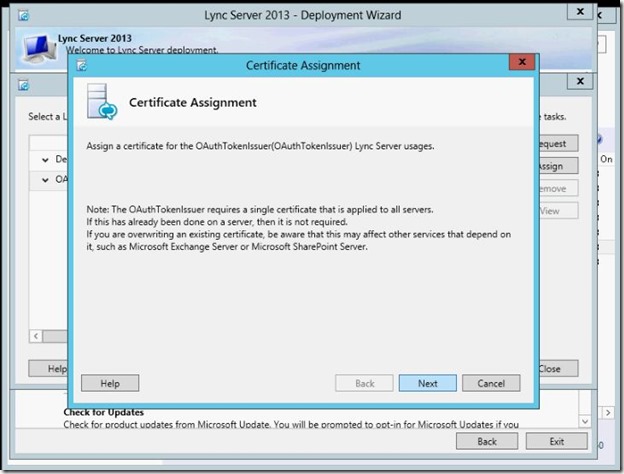
- Select the Certificate that you just created, you can View the Certificate here to confirm that you are selecting the correct certificate that has both Lync servers listed in the SAN.
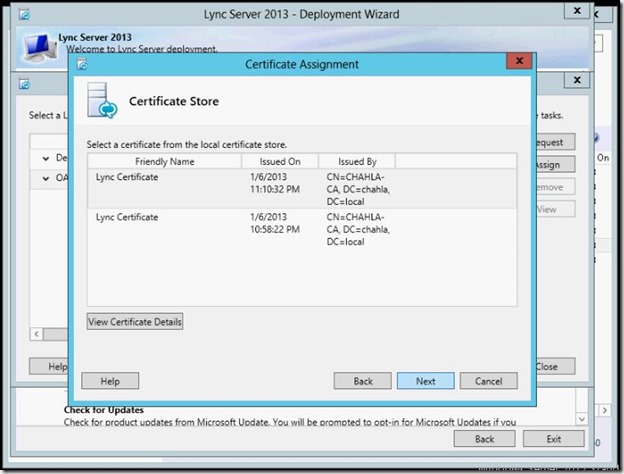
- Review the summary, then click Next.
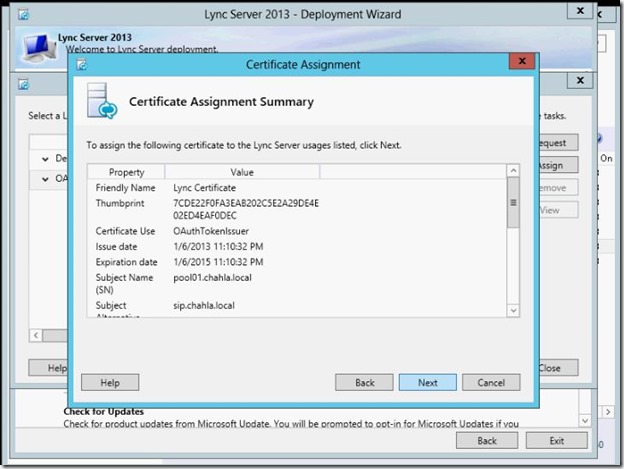
- Certificate Assignment is completed, click Finish.
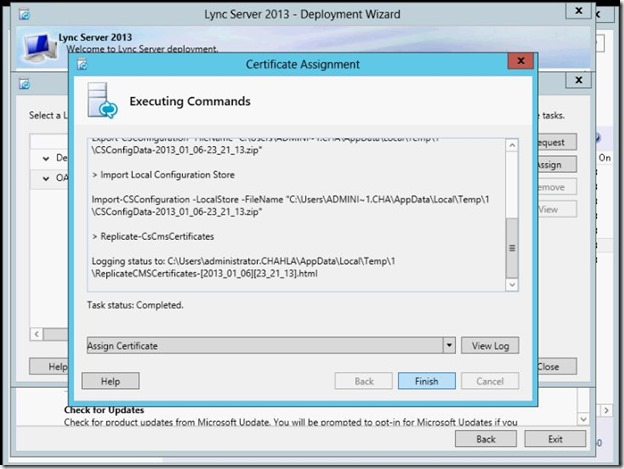
- Make sure you install the same certificate on both servers.
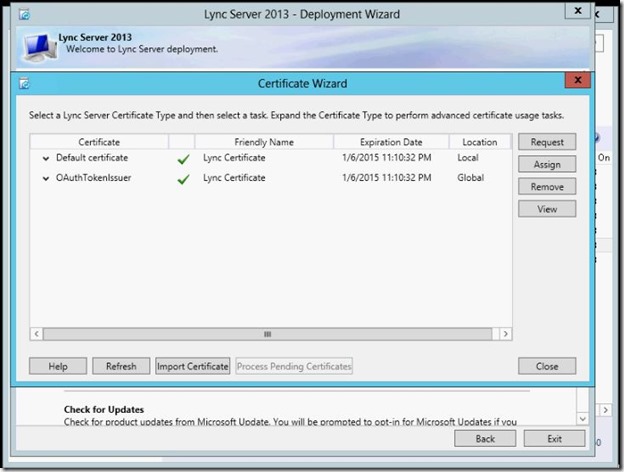
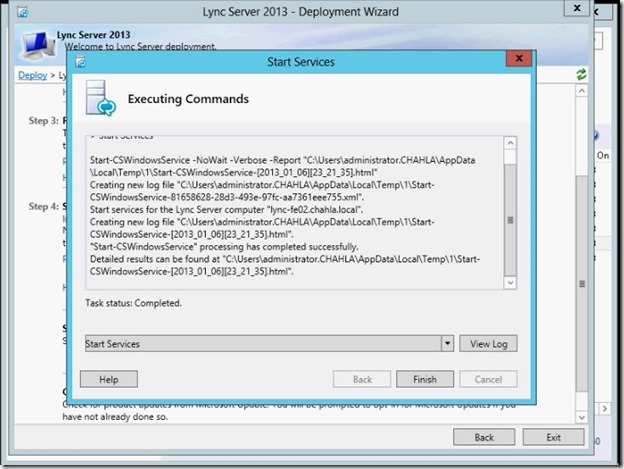
- Next, start the services.
- Services successfully started.
- And you can see the status at the Topology section in the Lync Control panel.
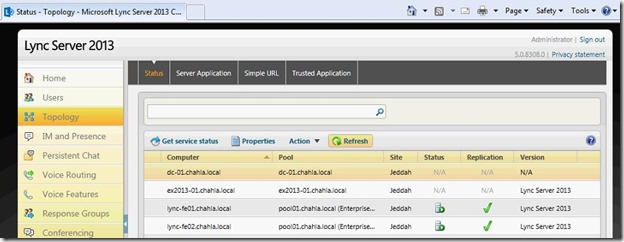
Done.
Servers :
DC-01.chahla.local (Domain Controller, Certificate Authority)
Lync-fe01.chahla.local (Lync Front End Server 01)
Lync-fe02.chahla.local (Lync Front End Server 02)
SQL-01.chahla.local (SQL Back End Server 01 for RTC Instance)
SQL-02.chahla.local (SQL Back End Server 02 for LyncMonitoring, LyncArchiving and Persistent Chat Instances) (not used in this article – i will be using it for other articles)
Pre-requisites:
-Active Directory, DNS, Active Directory Certificate Services (Certificate Authority)
(From Dashboard – > Add Roles And Features)
http://technet.microsoft.com/en-us/library/gg398686.aspx
Features
.NET Framework 3.5 Features (All)
.NET Framework 4.5 (ALL)
Message Queuing
Message Queuing Services
Remote Server Administration Tools
Role Administration Tools
AD DS and AD LDS Tools
User Interface and Infrastructure
Desktop Experience
Windows Identity Foundation 3.5
Web Server (IIS)
Role Services
Common Http Features Installed
Default Document
HTTP Errors
Static Content
Health and Diagnostics
HTTP Logging
Logging Tools
Tracing
Performance
Static Content Compression
Dynamic Content Compression
Security
Request Filtering
Client Certificate Mapping Authentication
Windows Authentication
Application Development
.NET Extensibility 3.5
.NET Extensibility 4.5
ASP.NET 3.5
ASP.NET 4.5
ISAPI Extensions
ISAPI Filters
Management Tools
IIS Management Console
IIS Management Scripts and Tools
Restart the server after installing the prerequisites.
- Open the installation media, Microsoft Visual C++ 2012 Redistributable will be installed when you launch the installer.
- Browse to the location where you want to install and click Install.

- Accept the EULA.

- Core components will install.


- Lync Server 2012 – Deployment Wizard will appear.

- The first thing that we will do is to Prepare Active Directory. Click Prepare Active Directory.

- On the right side of Prepare Schema, click Run.


- Click Next.


- Schema preparation finishes, click Finish.

- On the right side of Prepare Current Forest, click Run.

- Click Next.

- Select Local Domain, then click Next.


- Forest preparation finishes, click Finish.

- On the right side of Prepare Current Domain, click Run.



- Domain preparation finishes, click Finish.


- Add users to provide administrative access
On the Domain Controller, Open Active Directory Users And Computers

- Open the Security Group CSAdministrator and add the user who will be the Lync Administartor, i am using the Administrator account for this.


- Chahla\Administrator is now a member of CSAdministrator Group.

- Install RTC Instance on SQL01.chahla.local
- Open setup from the installation media.

- .Net Framework will be enabled.

- Planning page.

- Click on the Installation Menu, then select “New Installation or add features to an existing installation”.

- Support files setup, click Ok.

- Accept the license terms, then click Next.


- Check if you have errors, do not proceed until you fix them, otherwise click Next.

- Select SQL Server Feature Installation, then click Next.

- From the list of features select “ Database Engine Services, Management Tools-Basic, Management Tools –Complete” , browse where you want to install, then click Next.


- In the Instance Configuration, select “Named Instance” and name it RTC, then click Next.


- You can create service account for this step, i created sqladmin account.

- Select Windows authentication mode, then add the users that you want to grant them unrestricted access to the Database Engine, i added Administrator and SQLAdmin, click Next.


- Click Install.


- Done.

- Install Monitoring & Archiving DB instances on SQL02.chahla.local


- Named Instance: LyncMonitoring (any name)


- Another new installation, Named Instance: LyncArchiving (any name)

- Now you have to allow access to some ports in each sql server
On SQL-01, open SQL Server configuration Manager.

- click on Protocols for RTC, right click TCP/IP and hit Properties.

- Click on the IP Addresses tab, then at the bottom of the list you will see the TCP Dynamic Ports value used by RTC Instance. (49279 in my case)

- Open Windows Firewall, and click New Rule.

- Select Port, then click Next.

- select TCP, type the port number that you obtained in the previous step (49279), then click Next.

- Allow the connection, click Next.

- Apply it to all profiles, click Next.

- Give it any name, then click Finish.

- On the same server you have to open port UDP 1434 that is used by SQL

We will do the same on SQL-02 for the other two Instances (LyncMonitoring & LyncArchiving)
- for LyncMonitoring.

- Port is 49292 in my case.

- allow it in the firewall.

- give it a name.

- For LyncArchiving.

- Port is 49345 in my case.

- Allow it in the firewall.

- Give it a name.

- Also don’t forget to allow UDP 1434.

Now we will add some required DNS Records, create new Host (A or AAA)

- Type the name and the IP Address of the first Front-end Server, do this for:
meet.chahla.local
admin.chahla.local
dialin.chahla.local
pool01.chahla.local

- Now we will create a Service Location record (SRV), right click and select “Other New Records…”

- Select Service Location (SRV).


- Service: _sipinternaltls
Protocol: _tcp
Port Number: 5061
Host: pool01.chahla.local

- The Next step is to create Lync File Share
i will create mine on DC-01.chahla.local

- Share the folder.

- Give Everyone (Read) permission level, and the RTCComponentUniversalServices, RTCHSUniversalServices, RTCUniversalConfigReplicator, RTCUinversalServerAdmins (Read,Write) permission level.

- Back to the first Front End server, lync-fe01.chahla.local.
Open the Deployment Wizard, then click Install Administrative Tools.


- Next, we will create the Topology, open Lync Server Topology Builder.

- Select New topology, then click OK.

- Browse to the directory that you want to save the tbxml file, give it a name then click Save.

- The Create New Topology starts, click Next.

- On the “Specify additional supported domains” click Next.

- On the “Define the first site” page, type the name and the description of your first site then click Next.

- Specify site details, then click Next.

- At the last page of defining your topology, make sure the “Open the new Front-End Wizard” is checked, then click Next.

- Front End pool wizard starts, click Next.

- Select “Enterprise Edition Fron End Pool”, type the Pool FQDN then click Next.

- At this step, add your FE servers then click Next.

- Select the features that you want to enable then click Next. (i selected Archiving and Monitoring because i will be using later on)


- If you will use an Edge server, this is where you should define it.

- Click “New” to define a new SQL server store.

- Type the Server FQDN and the Name of the instance then click Ok.

- Click next.

- Now define the File store that you created and shared before.

- Select “Define a new file store”, type the FQDN of the server holding that shared folder, and the name of the folder then click Next.

- Here you can specify the External URL for the Web Services, i am not going to use it externally, so i will keep it as is.

- This step to define an Office Web Apps Server if you have one.

- Next, i will define a new Archiving and Monitoring Store for later on use.
Select New.

- Type the SQL Server FQDN, Select “Named Instance”, type the name of the instance and click OK. (if you are mirroring your instance you can check that option and type the port number there”

- the archiving store appears, click Next.

- The same thing for Monitoring, New store.

- Server FQDN and Instance Name.

- Store appears, click Finish.

- After you finished the wizard you need to edit the Administration URL.

- Right Click to edit the properties of your topology, click Edit Properties.

- Click “Simple URLs”

- in the “Administrative access URL” type the admin URL (https://admin.chahla.local in my case) and click OK.

- Then Publish the Topology.

- Click Next.

- Click Next.

- Click Next.







- Succeeded with warning, we will see the warning details.


- the warnings are because of the default settings of SQL Server, you can simply ignore it.



- Next step is to Install Local Configuration Store & Lync Server Components on Lync-FE01
Open the Deployment Wizard, and click “Install or Update Lync Server System”

- On the right side of Step 1 click Run.

- Select “Retrieve directly from the CMS,,,,” then click Next.



- Step 1 completed, click Finish.

- Step 2, Run.



- Step 2 completed, click Finish.

- Now we need to Request And Assign Certificate, Step 3 click Run.

- Click Request.


- Select “Send the request immediately to an online certification authority”

- Select your CA.

- click Next.

- click Next.

- type a Name for your Certificate, select the Bit Length and click Next.

- Fill in the Organization name and unit then click Next.

- Fill in the Geographical info and click Next.


- Select your sip domain, then click Next.

- Here you can add additional Subject Alternative Names.

- the request is completed, click Next.

- Make sure the “Assign this certificate to lync Server ,,,,” is checked then click Next.




- Certificate Assignment is completed, click Finish.


- Open your browser and type the admin url or pool url then /cscp , type your credentials and hit OK.

- You are done with the first FE server.

- Install Second Front End Lync-FE02.chahla.local (make sure you install the prerequisites same as FE01)

- Install Local Configuration Store, then Lync Server Components.

- Then request or import a certificate. (you can import the certificate that you created for FE01 if you added the name of the second front end server in the certificate SAN and if you checked the option to make the key as exportable")

- Request a certificate.





- Make sure you check the option “ Mark the certificate’s private key as exportable”, type the name then click Next.





- Add the second FE server.

- Make sure both servers are listed, then click Next.

- Certificate Request is done, click Next.

- Make sure “Assign this certificate to Lync Server …..” then click Finish.

- Certificate Assignment wizard opens.


- Assignment is ok, click Finish.

- Select OAuthTokenIssuer then click Assign.

- Click Next to Assign.

- Select the Certificate that you just created, you can View the Certificate here to confirm that you are selecting the correct certificate that has both Lync servers listed in the SAN.

- Review the summary, then click Next.

- Certificate Assignment is completed, click Finish.

- Make sure you install the same certificate on both servers.

- Next, start the services.

- Services successfully started.

- And you can see the status at the Topology section in the Lync Control panel.

Done.
No comments:
Post a Comment